On November 22nd Palo Alto Networks (PAN) published a Threat Brief on ‘Lunar Peek Operation’ [1]. The report detailed two recent vulnerabilities in their PAN-OS software and revealed the continuing risk from flaws in widely deployed perimeter security devices like firewalls and VPN gateways. These vulnerabilities, if left unpatched, expose organizations to serious threats from cybercriminals and state-sponsored threat actors. Palo Alto Network’s position as a leading provider of cybersecurity products and services to large commercial and government customers makes their customers high-value targets (HVT) and compounds the risk. Findings from credible security researchers like Shadowserver show that hundreds of vulnerable devices have already been compromised (exploited), highlighting active exploitation of these vulnerabilities.
In this post, we will:
- Provide an overview of these vulnerabilities and their significance.
- Review statistics and trends on compromised devices.
- Share recommendations and examples of how cybersecurity teams can use CTI and Generative AI (GenAI) to plan for, respond to, mitigate, and monitor vulnerabilities and threats.
Bottomline: Notwithstanding statistics from Shadowserver that show a decline in the number of compromised machines, the nature of the vulnerability and the profile of Palo Alto Networks (PAN) customers makes Lunar Peek Operation a dynamic and serious threat that warrants continued monitoring by cybersecurity teams.
Overview: CVE-2024-0012 and CVE-2024-9474
The Lunar Peek Operation highlights two related vulnerabilities in Palo Alto Networks products.
CVE-2024-0012 (Authentication Bypass) [2]: Enables an unauthenticated attacker with network access to the management web interface to gain PAN-OS administrator privileges to perform administrative actions, tamper with the configuration, or exploit other authenticated privilege escalation vulnerabilities like CVE-2024-9474.
- Severity: CVSS 9.3 (Critical).
- Urgency: Highest.
- Date: Updated 2024-11-23.
CVE-2024-9474 (Privilege Escalation) [3]: A privilege escalation vulnerability in Palo Alto Networks PAN-OS software allows a PAN-OS administrator with access to the management web interface to perform actions on the firewall with root privileges. This flaw is particularly dangerous when chained with CVE-2024-0012.
- Severity: CVSS 6/9 (Medium).
- Urgency: Highest.
- Date: Updated 2024-11-23.
Implications for Security Posture: The critical nature of these vulnerabilities lies in their ability to compromise the foundational security of an organization’s perimeter. Firewalls and VPN gateways are central to enterprise security architecture, and exploiting these devices could provide attackers with:
- Administrative Access: Allowing reconfiguration, disabling security measures, or backdooring the network.
- Pivoting Capabilities: Attackers could use compromised devices to move laterally within the network.
- Supply Chain Risks: Managed service providers or third-party vendors running vulnerable PAN-OS versions could inadvertently expose their customers to risks.
Threat Scope: The reporting on Lunar Peek covers various indicator types, including:
- Exposed Devices: Early reports from Shodan and Censys identified over 13,000 PAN-OS devices exposed to the internet, although not all were vulnerable (THN, Nov 21).
- Exploited Devices: Shadowserver Foundation’s dashboard tracked over 574 compromised devices in the U.S. on November 20, dropping to 89 by November 26 due to ongoing remediation (Shadowserver).
- Threat Actor Activity: Palo Alto’s Unit 42 reported active scanning and exploitation attempts targeting the vulnerabilities and published Indicators of Compromise (IOCs) to aid detection (Unit 42).
Compromised Devices
Much of reporting on compromised devices is based on reporting from Shadowserver, an authoritative source of Cyber Threat Intelligence.
Shadowserver Coverage: Shadowserver is a non-profit security research organization that continuously scans the IPv4 Internet, operates honeypots and sinkholes, and provides data on exposures and compromised devices through a dashboard. Shadowserver was the source of oft-cited statistics of over 2,000 compromised devices worldwide by other researchers and journalists. [7-12] Additionally Shadowserver was one of the first sources cited (Nov 12), for reporting close to 11,000 exposed PAN-OS devices management devices. [13]
Shadowserver Dashboard: The Shadowserver dashboards provides the ability to use filters and tags for database queries. In Figure 1 we see the query for ‘panos-compromised’ websites resulted in 554 devices in the U.S.
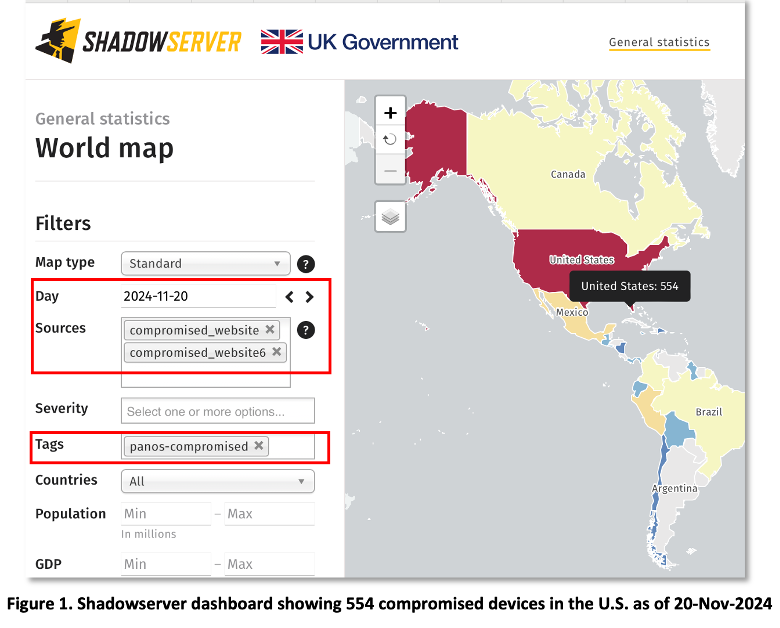
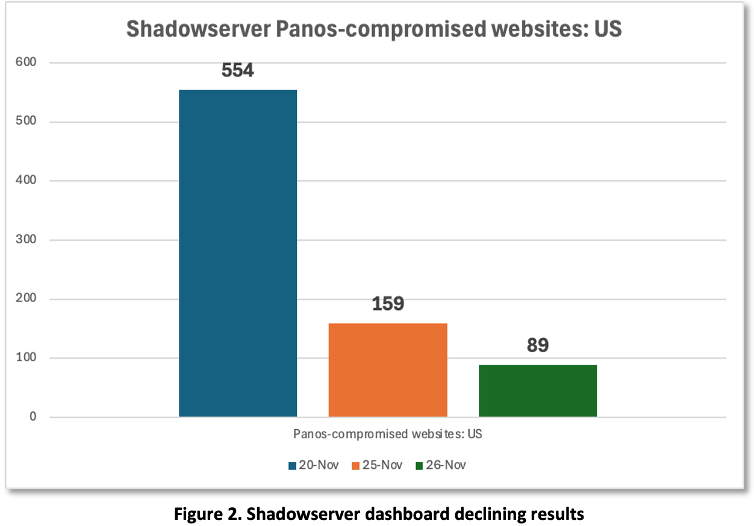
In Figure 2, we see three snapshots from Nov 20, 25, and 26 showing a clear downward trend in panos-compromised websites. The decline is encouraging and perhaps attributed to a combination of patching, mitigation efforts, and network hardening. However, before we can conclude that the threat has abated entirely, there are reasons for caution. Given the lag between vulnerability discovery and exploit reporting, the threat may be dormant. With 10,000 potentially vulnerable devices and more adversaries developing exploits, more devices could be exploited. Further, Shadowserver only tracks visible compromised devices. Devices compromised by more advanced threat actors may evade detection, especially if attackers disable logging or avoid noisy exploitation techniques.
Recommendations for Cybersecurity Teams
Enterprise cybersecurity teams are overwhelmed by the volume of cyber alerts generated by their SOCs (Security Operations Centers), as well as the volume and tempo of cyber threat intelligence on vulnerabilities and threats from their feeds and open sources. The problem is more complex for teams responsible for monitoring risks to their third-party relationships (supply chains) or in their industry sectors.
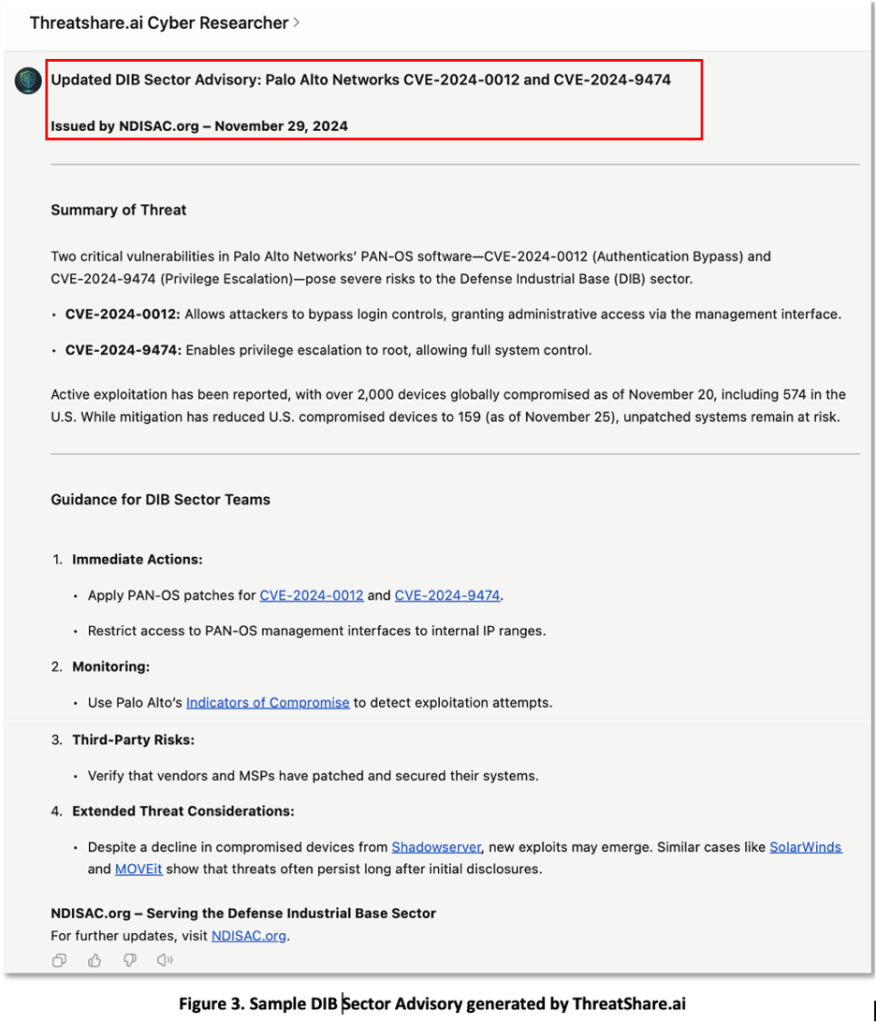
Generative AI (GenAI) can help security teams analyze and prioritize cyber threat intelligence most relevant to their networks and operations. Below are two examples relevant to teams in critical infrastructure sectors or supporting Information Sharing and Analysis Centers (ISACS). In Figure 3, we see a hypothetical ‘Sector Advisory’ for the Defense Industrial Base (DIB) that might be generated by the responsible sector ISAC (Information Sharing and Analysis Center), which for the DIB could be NDISAC (National Defense ISAC).
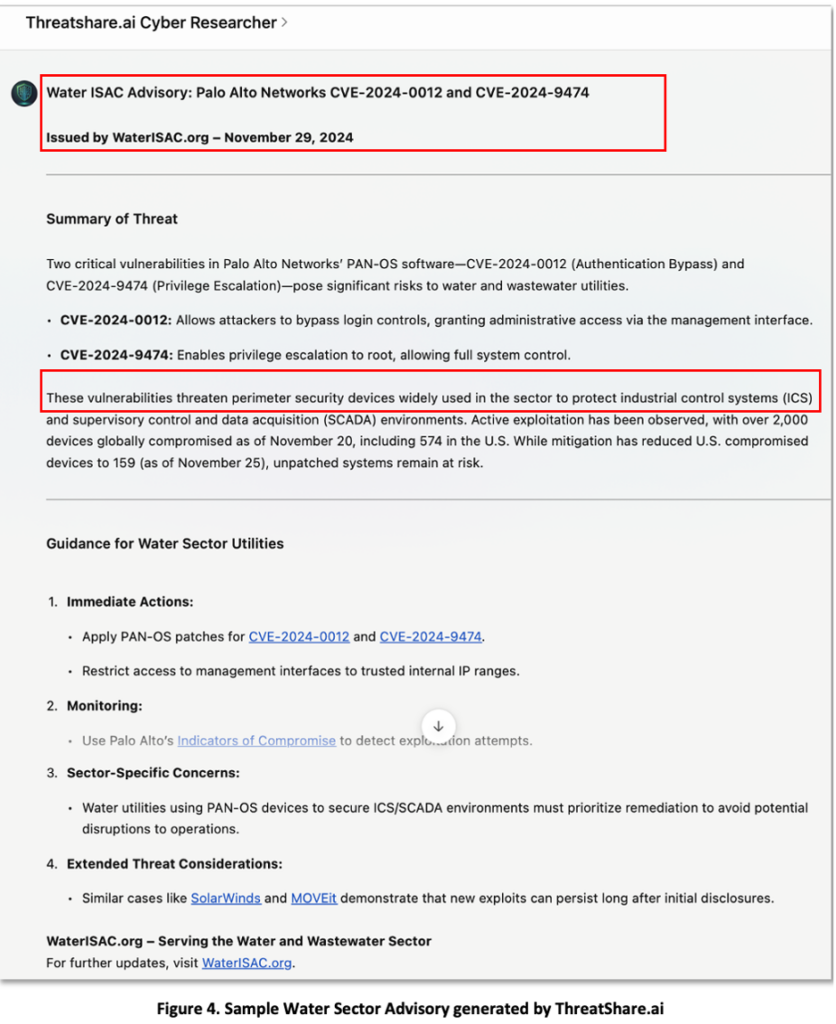
in Figure 4, we see a hypothetical ‘Sector Advisory’ report for the Water ISAC. In this case note that the GenAI generated sector-relevant guidance on Industrial Control Systems (ICS or SCADA) which are relevant to this sector.
Conclusion
The exploitation of CVE-2024-0012 and CVE-2024-9474 demonstrates the complexities of responding to high-profile vulnerabilities. Organizations must act quickly to secure their networks while monitoring broader trends in their sectors or supply chains. CTI (Cyber Threat Intelligence) teams need to anticipate evolving threats, monitor risks in their sectors and supply chains, and continuously refine their intelligence capabilities.
Extended Attack Surface Management (EASM) systems from vendors like Palo Alto Networks, CrowdStrike and Microsoft provide visibility of an organization’s external digital assets and vulnerabilities and are an important and proactive measure. EASM tools that integrate Dark Web monitoring and network telemetry analysis from products like TacitRed hold promise, as do solutions for building sector risk intelligence on platforms like Redbrick and Snowflake. [14-16]
Generative AI tools are a powerful and versatile part of the solution mix. Among other things, GenAI can help cybersecurity teams conduct research, build and enrich intelligence collections, generate reports, and train their teams. By integrating GenAI into their processes, cybersecurity teams can improve their abilities to analyze complex data, identify emerging risks, respond with speed and precision, and better protect their organizations, supply chains, and sectors against evolving threats and persistent adversaries.
Editor’s Note:
- Credit to our chatbots for their valuable assistance with threat analysis research, proofreading, and editorial review.
References
- Palo Alto Networks: Unit 42 – VULNERABILITIES Threat Brief: Operation Lunar Peek, Activity Related to CVE-2024-0012 and CVE-2024-9474 (Updated Nov. 22) , updated 22-Nov-2024
- Palo Alto Network – CVE-2024-0012 PAN-OS: Authentication Bypass in the Management Web Interface (PAN-SA-2024-0015), updated 23-Nov-2024
- Palo Alto Network – CVE-2024-9474 PAN-OS: Privilege Escalation (PE) Vulnerability in the Web Management Interface, updated 20-Nov-2024
- Github.com: Palo Alto NetworksUnit42-Threat-Intelligence-Article-Information – 2024-November-IOC-updates-OperationLunarPeek.txt , Nov 2024
- Watchtowr Labs – Pots and Pans, AKA an SSLVPN – Palo Alto PAN-OS CVE-2024-0012 and CVE-2024-9474, 19-Nov-2024
- The Shadowserver Foundation: Dashboard – tag=panos-compromised, 20-Nov-2024
- BleepingComputer – Over 2,000 Palo Alto firewalls hacked using recently patched bugs, 21-Nov-2024
- Cybersecurity Dive, Matt Kapko – Palo Alto Networks pushes back as Shadowserver spots 2K of its firewalls exploited, 22-Nov-2024
- Wiz – Wiz observes exploitation in the wild of PAN-OS vulnerabilities, 22-Nov-2024
- Arctic Wolf – Arctic Wolf Observes Threat Campaign Targeting Palo Alto Networks Firewall Devices, 22-Nov-2024
- Help Net Security – 2,000 Palo Alto Networks devices compromised in latest attacks, updated 23-Nov-2024
- THN (The Hacker News) – Warning: Over 2,000 Palo Alto Networks Devices Hacked in Ongoing Attack Campaign, 21-Nov-2024
- The Stack – Palo Alto Networks warns over possible PAN-OS RCE: Says get your blooming interface off the internet, 12-Nov-2024
- TacitRed – https://tacitred.com/product/
- Databricks – Detecting Criminals and Nation States through DNS Analytics https://tacitred.com/product/
- Snowflake – THE AI DATA CLOUD FOR CYBERSECURITY
