On 22-October-2024, The Computer Emergency Report Team of Ukraine (CERT-UA) and Amazon issued Cyber Threat Intelligence (CTI) alerts. Microsoft followed with a detailed blog post on 29-October. These alerts described a targeted phishing and espionage operation over a wide attack surface, affecting government, military, NGO, and industry targets in Europe, Israel, Japan, and the U.S. The campaign leveraged AWS and government themed domain names as lures to steal Windows credentials by exploiting Microsoft Remote Desktop (RDP).
In this post, we cover:
- An overview of APT29
- A summary of the APT29 AWS-RDP campaign
- Additional CTI not found in the CERT-UA, AWS, or Microsoft reports on the cyber infrastructure used
- Examples of how cyber threat researchers can use CTI and GenAI (generative AI) to gain deeper insight into adversary and campaign details
- An outlook on RDP exposures and vulnerabilities in NATO countries.
Bottom line: APT29 remains a highly skilled and persistent adversary supported by the Russian government. An unusual aspect of this campaign was the broad scope of the attack surface. No definitive reports on victimology or impacts have been released, as espionage impact assessments often take time. For now, the campaign serves as a reminder for organizations that meet the targeting profile to restrict and monitor their Microsoft Remote Desktop (RDP) connections.
APT29 Overview
Before examining the AWS-RDP campaign, here’s some context on APT29. For more details, see references [4-10].
APT29 (AKA Midnight Blizzard, Cozy Bear, Nobelium), is a sophisticated cyber espionage group linked to the Russian Foreign Intelligence Service (SVR). Active since 2008, APT29 has targeted governments, military organizations, NGOs, think tanks, technology companies, and healthcare institutions globally. Known for its stealth, precision-targeting, and advanced tactics, APT29 has executed numerous operations using spear-phishing, supply chain compromises, and cloud-based attacks.
A search using GPT-4o estimates that APT29 has conducted at least 30 campaigns, including high-profile attacks like the U.S. Democratic National Committee (DNC) in the 2016 elections, and the SolarWinds and TeamCity software supply chain attacks. [4, 7] Recently, the group has focused on exploiting cloud infrastructure and harvesting credentials from government and diplomatic entities, especially in NATO-aligned countries. As noted in a Joint Cyber Advisory from October 2024: “Since at least 2021, Russian SVR cyber actors … have consistently targeted US, European, and global entities in the defense, technology, and finance sectors to collect foreign intelligence and enable future cyber operations, including in support of Russia’s ongoing invasion of Ukraine since February 2022. Their operations continue to pose a global threat to government and private sector organizations.” [6]
CTI analysts can use Generative AI to develop adversary intelligence. In Figure 1, we see an example of an APT29 adversary profile generated using ThreatShare’s customized GPT-4o for the cyber threat research domain. The prompt specifically requested a concise (under 300 words) and recent profile since January 2023.
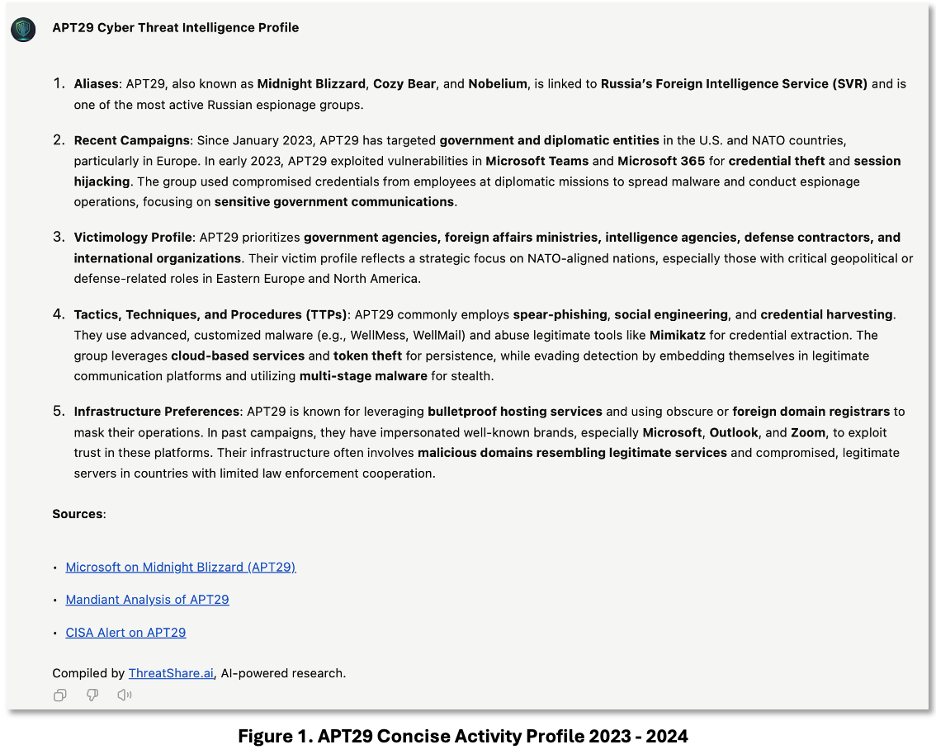
CERT-UA and Microsoft Reports
CERT-UA issued their initial report on October 22, 2024. The report detailed a phishing and espionage campaign that began in early August 2024, targeting government, military, and industrial organizations across NATO countries, Israel, Japan, and the U.S. The campaign used domain names with lexical and semantic relevance to cloud computing, AWS, zero trust architectures, government ministries, or security companies. AWS-themed domains were used as lures, but the real goal was to capture Microsoft Desktop (RDP) user credentials. CERT-UA and AWS disrupted the campaign, seized the domain names, and shared indicators of compromise with the CTI community [1-3].
In its report on October 29, Microsoft provided 15 additional domain indicators to the 96 previously identified by CERT-UA. Microsoft also provided insights into the targeting, noting that spear-phishing emails were sent to thousands of targets across more than 100 organizations and contained a signed Remote Desktop Protocol (RDP) configuration file that connected to actor-controlled servers. The use of a signed RDP configuration file to gain access to targets’ devices represents a novel vector for APT29. A screenshot of APT29’s RDP connection, as captured by Microsoft, is shown in Figure 2.
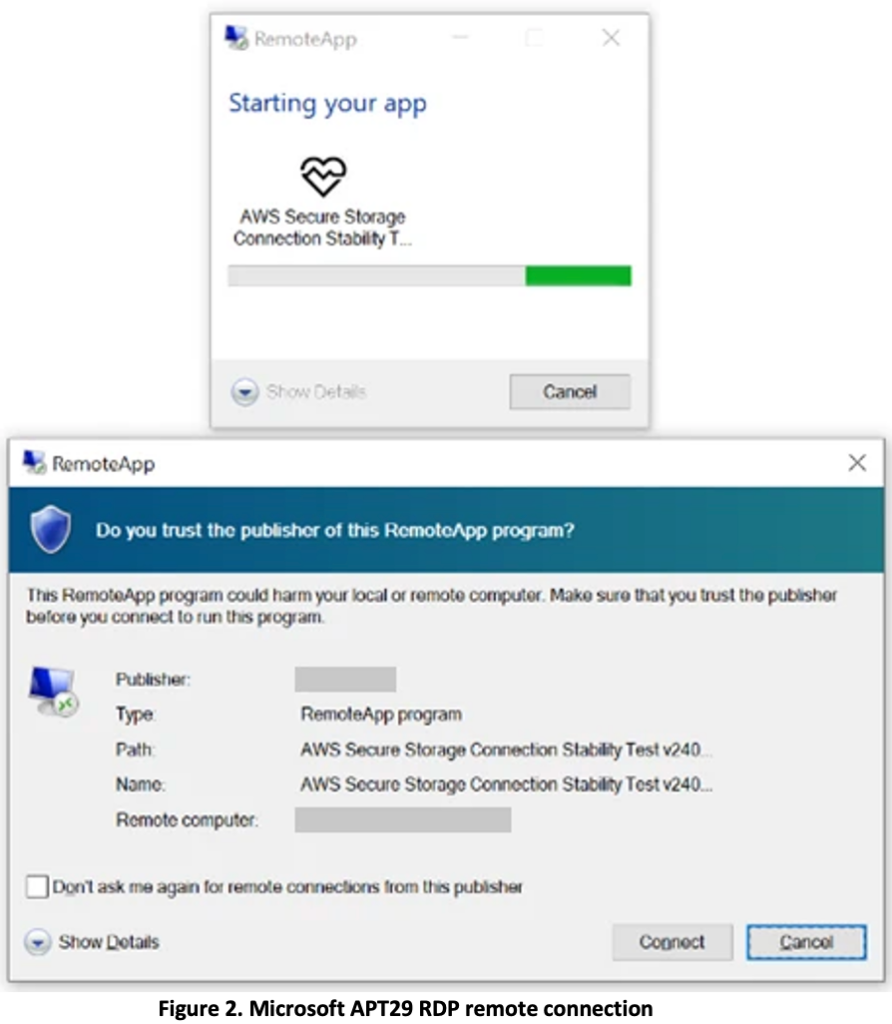
APT 29 RDP Campaign CTI
The sharing of threat indicators and knowledge of attacker TTP (tactics techniques and procedures) provides cybersecurity teams with the details needed to investigate systems for signs of compromise and mitigate future attacks.
The CERT-UA (October 22) and Microsoft (October 29) reports provided indicators of attack, including:
- 23 file indicators
- 111 domain names (second-level domains – SLDs)
- 36 IPv4 addresses
- 4 email addresses used to send the phishing emails
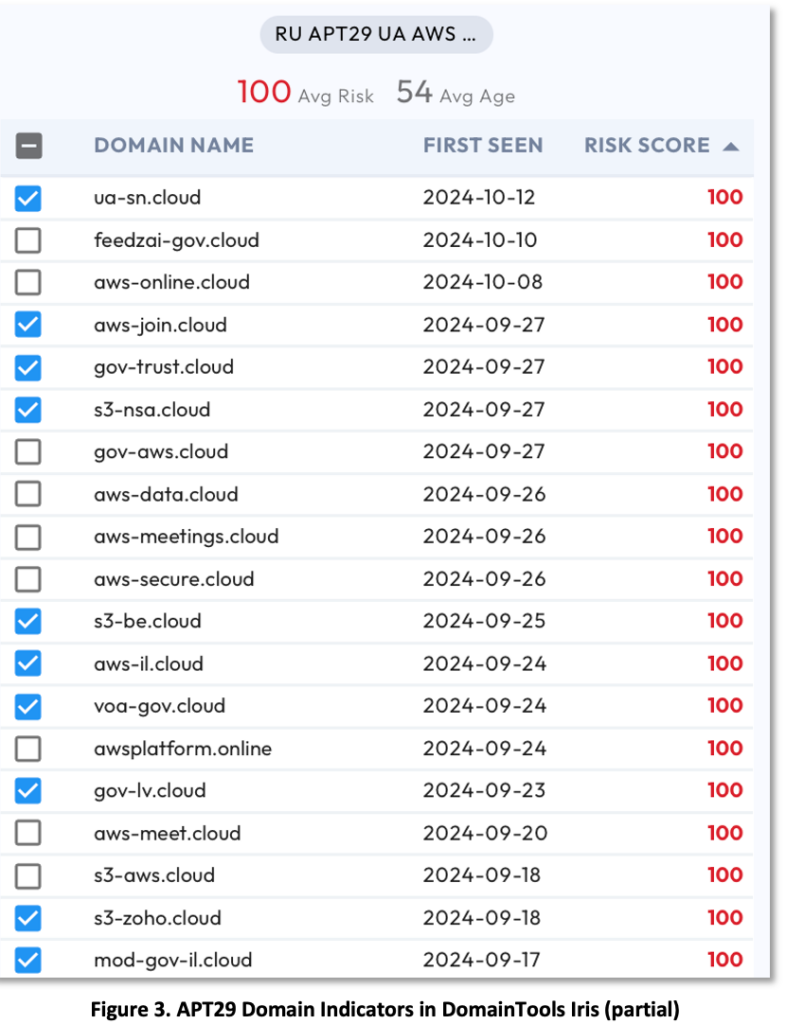
To CTI researchers, these indicators are a starting point for further investigation. We loaded the domain indicators and IPs into DomainTools and Virus Totals. Figure 3 shows a partial view the domains names, registration dates, and risk scores in DomainTools. From the ‘first seen’ column, it’s evident that these domains were newly registered.
Our analysis provides additional insights:
- IP addresses: Using Virus Total, 34 of the IP addresses provided by CERT-UA were rated as ‘malicious’ by at least one Virus Total feed, with 2 reported as ‘suspicious’.
- Domain name risk: DomainTools reports that 109 of the 111 domain names (98%) had a risk rating of 100 (on a scale from 1 to 100).
- Top-level-domains (TLD): 98% (109/111) used the ‘.cloud’ TLD.
- Newly registered domains: 62% of the domain names were registered in September/October 2024, with the remaining 38% registered in August 2024. Newly Registered Domains (less than 60-days) have elevated inherent risk.
- Domain Registrars: The top three registrars were Tucows (29%), NameSilo (19%), and eNom (16%). Cyber threat actors favor domain registrars with lax registration, payment and take-down policies.
- Internet Service Providers (ISPs) The top three ISPs were EDIS GmbH, AS9009 (Austria) at 20%, Public Services, AS24806 (Czech Republic) at 15%, and Kuroit Limited (UK) at 13%. The use of smaller European hosting providers across 23 different hosting services is atypical and complicates takedown efforts.
- IP geolocation: The top three countries hosting the domains were the US (43%), Czech Republic (18%), and the UK (9%).
- Shared hosting: 18% of the domain names resolved to the same IP address, 81.2.196[.]19 in the Czech Republic.
- Email addresses used to send phishing emails: APT29 used email addresses belonging to legitimate organizations, obtained during previous compromises. One such domain was ‘townoflakelure[.]com’—a small town in North Carolina impacted by Hurricane Helene and located in a U.S. swing state, suggesting potential links to election-related disinformation.
As Threat Actors develop preferences for certain infrastructure providers, understanding infrastructure usage provides insight into actor techniques and procedures (TTP) across campaigns.
CERT-UA GenAI Insights
In addition to traditional CTI, we also use GenAI tools (OpenAI’s GPT-4o, Perplexity.ai, Anthropic’s Claude, and ThreatShare’s customized GPT-4o) to support our analysis.
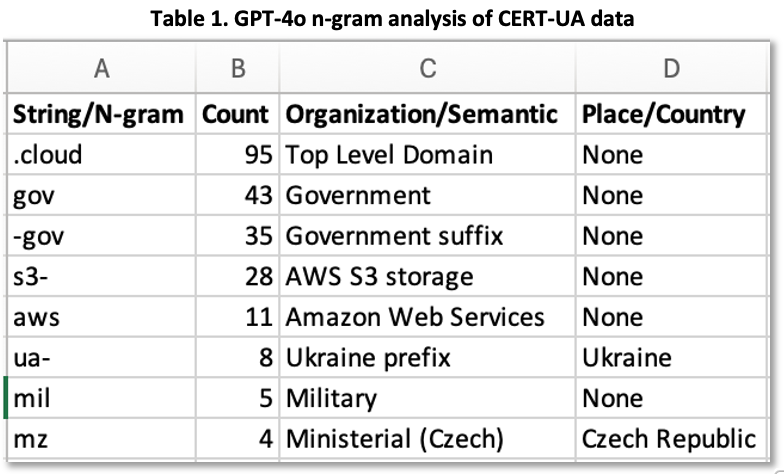
The NLP and semantic analysis capabilities of GenAI can offer CTI researchers additional perspectives beyond standard indicators. For instance, Table 1 shows GPT-4o results from n-gram (text string) analysis of the 96 domain indicators provided by CERT-UA.
Visualizations of this data, as shown in Figures 4 and 5, provide researchers with greater insights and reporting capabilities. These visualizations, generated using Anthropic’s Claude LLM, suggest patterns in the domain names and their relative prominence that may not be readily evident in text or data views.
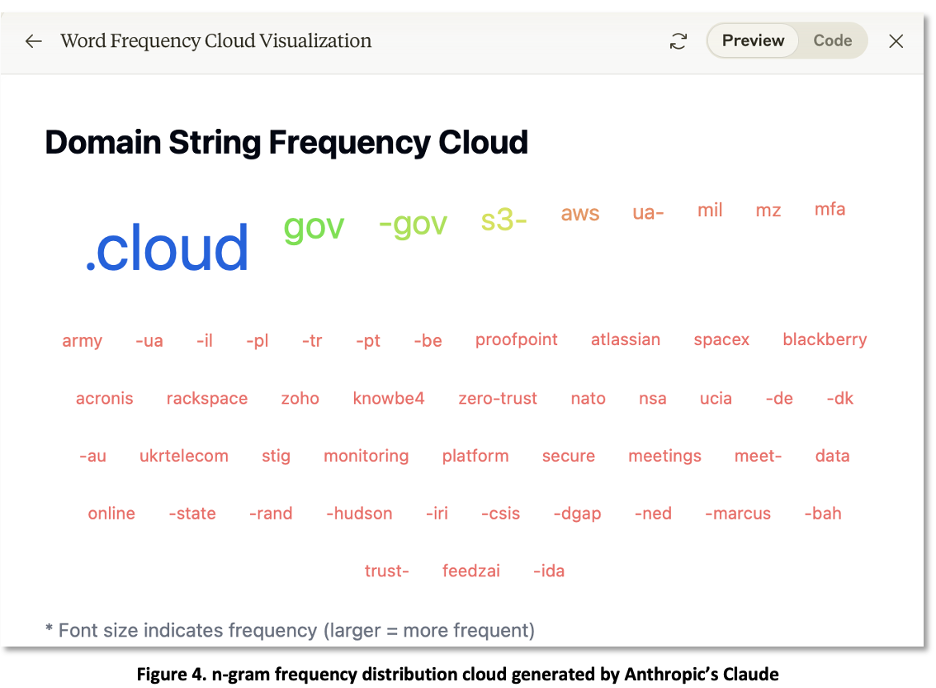
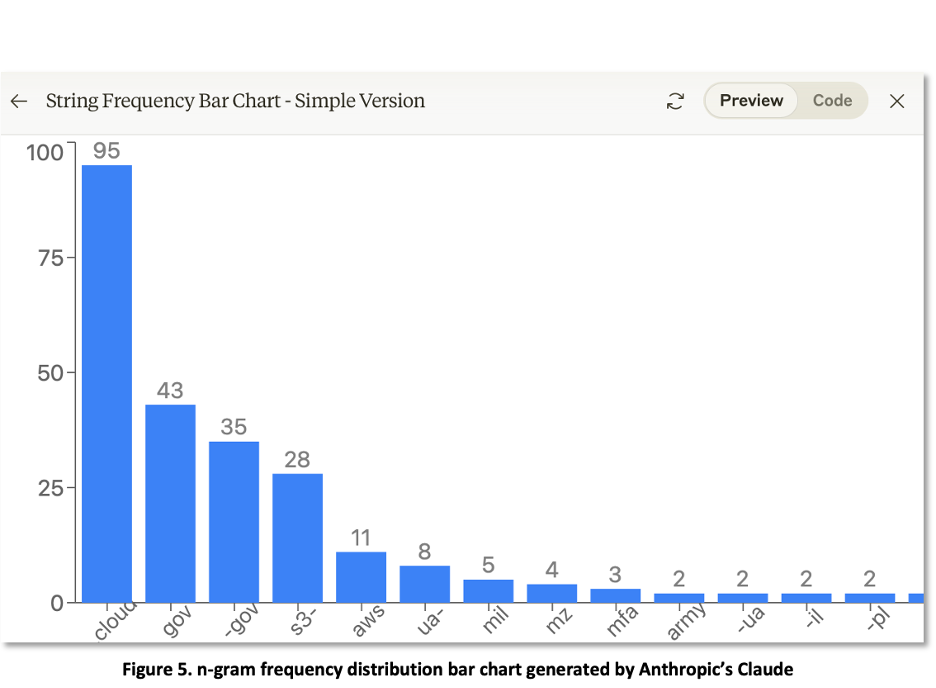
APT29 Outlook
APT29 is a skilled and persistent threat actor. Remote Desktop hosts remain high-value targets for APT29 and other adversaries. As APT29 continues to target NATO countries, we should anticipate more campaigns in the future.
Table 2, generated from Shodan, shows RDP exposures in various NATO countries (columns 1 and 2). Column 3 lists RDP indicators hosted by Stark Industries, a notorious bulletproof hosting provider used in multiple Russian campaigns, as noted in our previous research and in reports by KrebsonSecurity.com [11-12].
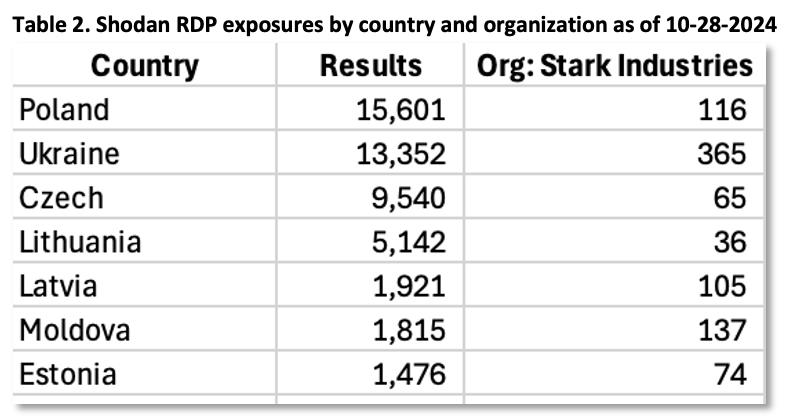
Sharing knowledge about attacker TTPs, network exposures, and verified vulnerabilities from sources like Shodan or Censys helps cybersecurity teams identify potential risks. The distribution of file and network indicators, as well as YARA rules from trusted CTI sources, enables teams to check system logs for indicators of compromise or attack, and implement appropriate blocking measures. For more information on remediation, see the Microsoft and CERT-UA reports [1,3].
Editor’s Notes:
- Credit to our chatbots for their valuable assistance with threat analysis research, proofreading, and editorial review.
- Featured Image source: IISF – Irish Information Security Forum, https://www.iisf.ie/SVR-cyber-actors-tactics-cloud-access
References
- CERT-UA: RDP configuration files as a means of obtaining remote access to a computer or “Rogue RDP” (CERT-UA#11690), 23-Oct-2024
- AWS: Amazon identified internet domains abused by APT29, 24-Oct-2024
- Microsoft Threat Intelligence Blog – Midnight Blizzard conducts large-scale spear-phishing campaign using RDP files, 29-2024
- MITRE ATT&CK: APT29, Last updated 12-April-2024
- SOCRadar – APT Profile: Cozy Bear / APT29, last update 11-Oct-2024
- Joint Cybersecurity Advisory (FBI, NSA, Cyber National Mission Force – CNMF, NCSC-UK) – Update on SVR Cyber Operations and Vulnerability Exploitation, 10-Oct-2024
- CISA, Alert Code AA23-347A: Russian Foreign Intelligence Service (SVR) Exploiting JetBrains TeamCity CVE Globally, December 13, 2023
- Microsoft – Nation State Actors Midnight Blizzard, 25-Jan-2024
- Recorded Future News: Kremlin-linked hackers target Ukraine’s state, military agencies in new espionage campaign , 25-Oct-2024
- Dark Reading: ‘Midnight Blizzard’ Targets Networks With Signed RDP Files , 30-Oct-2024
- ThreatShare.ai – Bulletproof Hosting Havens for FIN7 and Russian Cyber Threat Groups, 21-July-2024
- KrebsonSecurity.com – The Stark Truth Behind the Resurgence of Russia’s FIN7 , 10-July-2024
