We are now twelve days (July 18-29) into the CrowdStrike Outage incident. While its impact and scale may be unprecedented, recovery operations are winding down. In this follow-on to our July 24th Flash Report, we provide:
- A high-level After Action Report (AAR) on the scale and impact of the incident.
- An assessment and examples of threat activity reporting associated with the incident.
- An outlook on software supply chain risks with a focus on how Windows kernel drivers are used by security solution providers and exploited in adversary attacks.
- Examples of how cyber threat intelligence (CTI) analysts can use to GenAI to understand and generate reports related to threat and risk assessments.
CrowdStrike Outage AAR
Here’s a summary of the CrowdStrike Outage incident:
- The problem was acknowledged by CrowdStrike and caused by a defective content update for the CrowdStrike Falcon® sensor.
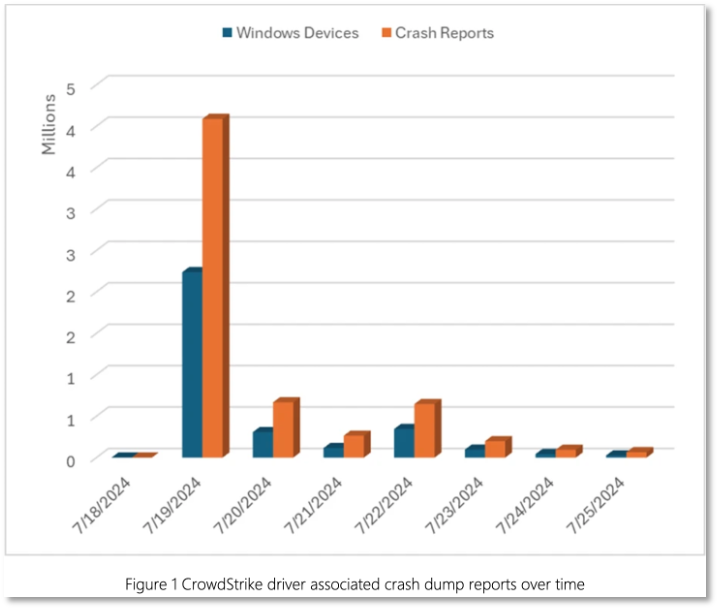
- The incident was initially reported as impacting 8.5 million Windows devices of CrowdStrike’s customers. On July 27th, Microsoft reported that the initial estimate of 8.5 million affected devices was based on a sample and likely undercounts the actual impact. [3, 4]. See timeline in Figure 1.
- Parametrix estimates that the total direct financial loss to US Fortune 500 companies (excluding Microsoft) from the CrowdStrike outage on 19 July will be $5.4 billion. Of this, only 10% to 20% of the loss will be covered by cyber insurance policies, with a weighted average loss of $44M per Fortune 500 company and up to $143 million for airlines. [2]
- CrowdStrike reported that 97% of Windows sensors were back online as of July 24 at 5pm PT. [5] Assuming a conservative estimate of 8.5M impacted Windows devices, that leaves 255,000 devices still offline for at least 7-days.
Threat Activity Reporting
Here’s a summary of some of the threat reporting from open sources and from our direct observation of newly registered domain (NRD) names using our DomainTools monitors.
- As of July 28th, CrowdStrike had issued at least five threat reports on its blog. [6 – 10] These reports include the unverified claims by the Hacktivist threat actor USDoD that it hacked one of CrowdStrike’s databases on threat actor groups. [10, 11]
- In addition to the authoritative cyber threat intelligence (CTI) reports we reported in our last report from SentinelOne and Flashpoint, we have seen some reports claiming more than 2,000 malicious domain name registrations associated with this incident. [13, 14] We believe these estimates may be inflated as they include URLs and subdomains, in addition to new domain registrations.
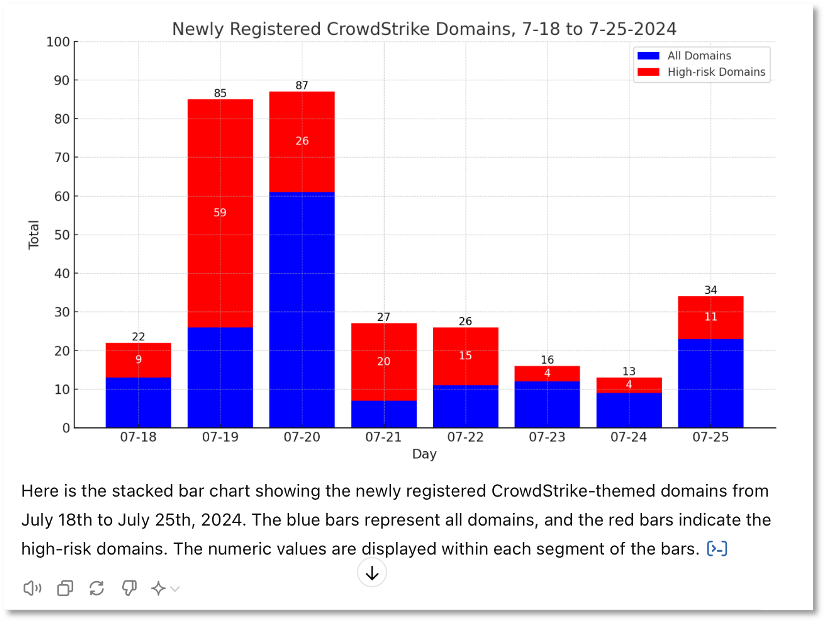
- In Figure 2, we see a summary of our own research on new domain registrations thematically associated with this incident for the period July 18-25. Our DomainTools advanced search found 310 total registrations for this period for domains containing the terms ‘CrowdStrike’ OR ‘Microsoft’. Of these, 149 are classified as high-risk, based on a DomainTools risk score of 80+ (as shown in red on the chart). These domains were likely registered as lures for phishing, to drive traffic, or parked for sale or future campaigns. The data for these charts was downloaded from DomainTools and summarized in Excel. The Excel summaries were uploaded to GPT-4 which generated the charts based on several natural language prompts.
Outlook
With Microsoft claiming that 97% of impacted devices are now back online, this incident appears to be mostly contained. Here is what we anticipate in the near term:
- Lawsuits and potentially class actions. [19]
- More threats – the NYTimes reports that this supply chain incident provides cybercriminals and nation-state threat actors a “detailed roadmap for disruption”. [18]
- More exploitation of inherent Windows kernel mode weaknesses by cybercriminals and nation state actors. As noted by Microsoft, CrowdStrike and many security software providers tradeoff the performance and tamper resistance benefits of Windows kernel drivers over resilience weaknesses. [4] Cyber threat actors have also made this trade-off. In May 2023, Fortinet and Trend Micro cyber threat researchers reported two campaigns by ransomware gang BlackCat (AKA Alphv) and Iranian threat actors that leveraged malicious kernel-level drivers. [17]
GenAI CTI Analyst Assistant
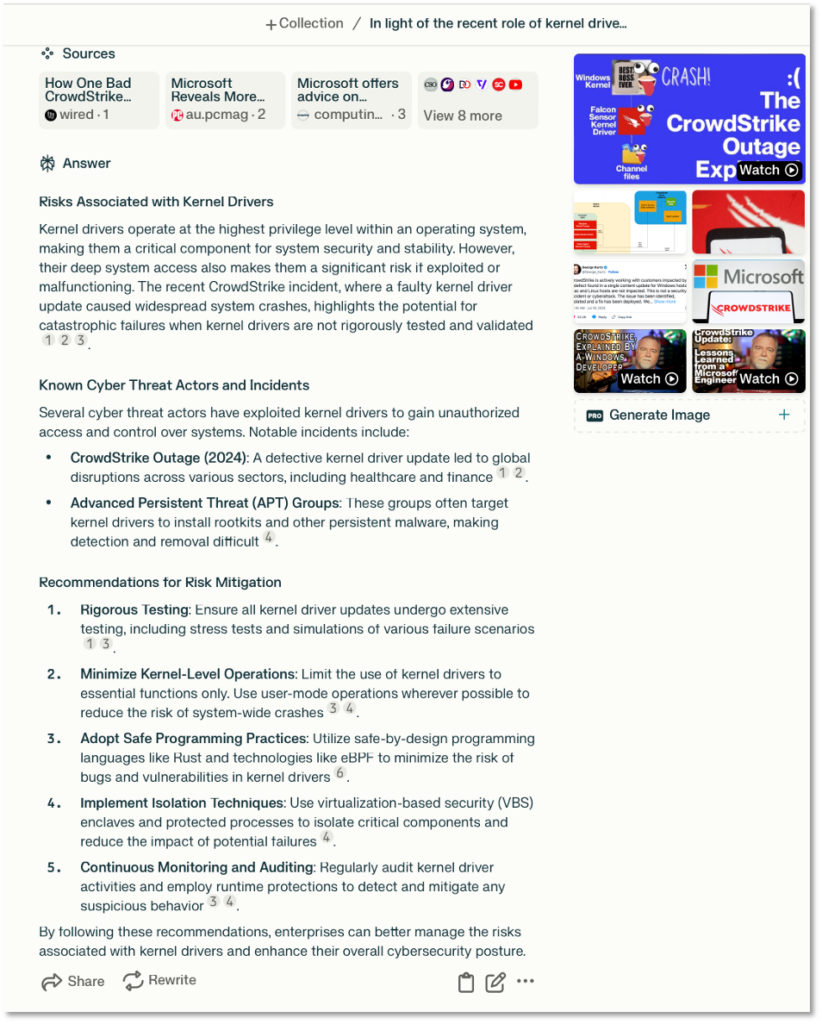
Previously we showed in Figure 2 how we used GPT-4 to simplify the generation of charts from the DomainTools threat data. In Figure 3 we show another analyst use-case – GenAI Assistant. In this case we used Perplexity.ai to draft a brief for the CISO on the risks, threats and risks associated with kernel drivers. While the analyst always needs to verify the results, the report seems reasonable at a glance. Generally, Perplexity.ai does a good job providing references and links to facilitate the verification process.
References
- Ars Technica – 97% of CrowdStrike systems are back online; Microsoft suggests Windows changes. , 26-July-2024
- Parametrix – CrowdStrike to Cost Fortune 500 $5.4 billion , 24-July-2024
- The Register – Microsoft admits 8.5 million CrowdStrike machines estimate was lowballed , 29-2024
- Microsoft Security – Windows Security best practices for integrating and managing security tools , 27-July-2024
- CrowdStrike – Preliminary Post Incident Review (PIR) , 27-July-2024
- CrowdStrike – Malicious Inauthentic Falcon Crash Reporter Installer Distributed to German Entity via Spearphishing Website , 25-July-2024
- CrowdStrike – Lumma Stealer Packed with CypherIt Distributed Using Falcon Sensor Update Phishing Lure , 24-July-2024
- CrowdStrike – Threat Actor Distributes Python-Based Information Stealer Using a Fake Falcon Sensor Update Lure , 23-July-2024
- CrowdStrike – Threat Actor Uses Fake CrowdStrike Recovery Manual to Deliver Unidentified Stealer , 22-July-2024
- CrowdStrike – Hacktivist Entity USDoD Claims to Have Leaked CrowdStrike’s Threat Actor List , 25-July-2024
- Outpost24 – Threat group USDoD claims to leak CrowdStrike threat actor database , 25-July-2024
- Windows Central – Microsoft wants to make future CrowdStrike outages impossible, and it could mean big changes for security software , 26-July-2024
- Dark Reading – CrowdStrike ‘Updates’ Deliver Malware & More as Attacks Snowball , 25-July-2024
- URLscan.io – https://urlscan.io/search/#crowdstrike*%20date%3A%3Enow-7d%20 , 25-July-2024
- ANY.RUN Blog – Find Threats Exploiting CrowdStrike Outage with TI Lookup , 23-July-2024
- Wikipedia | CrowdStrike – CrowdStrike – Severe_outage_incidents
- TechTarget – Threat actors leverage kernel drivers in new attacks , 23-May-2023
- NYTimes – What Happened to Digital Resilience?, 19-July-2024
- Parker | Waichman LLP – CrowdStrike Lawsuits Filed Following Global IT Outage
