We are now in day 6 (July 18 – 23) of the Internet outage caused by a defective CrowdStrike software update. In this post, we focus on one aspect of the story – the tracking, discovery, and analysis of event-themed domain names that have been registered since the event and are considered threats based on their behavior or reputation from trusted threat feeds. The purpose of this Flash Report is to share:
- Summary of the CrowdStrike Outage incident.
- Aggregated threat feeds of malicious domain names from CrowdStrike, Flashpoint, and SentinelOne.
- DNS Intelligence methods for discovering malicious domains thematically related to this incident. Our examples are based on DomainTools Iris. Of close to a thousand newly registered domain names thematically relevant to the CrowdStrike Outage incident, we have identified 77 unique domain names with high-risk scores (80-100) registered between 7-19 and 7-23. Key finding: we discovered more malicious domains through our custom advanced queries than third-party threat feeds.
- Word frequency distribution stats from GenAI methods that can be used as feedback for new queries.
Event Summary
On July 18th, CrowdStrike released a defective content update for the CrowdStrike Falcon® sensor which effectively bricked 8.5 million Windows devices across the globe, sending them into a BSOD (Blue Screen of Death) loop. [1,2] Even though the defective file was only available for a 1-hour window, the consequences were severe, causing millions of enterprise systems to crash with cascading effects rippling across critical infrastructure sectors in aviation, hospitals, financial services, government, and manufacturing. [3] CrowdStrike confirmed the issue and accepted responsibility on July 19. [6] This event was not caused by a cyber-attack. Rather, it is attributed to human error – a defective CrowdStrike software update and testing process failure that resulted in the defective software being pushed in an automatic update to CrowdStrike’s 29,000 customers. While CrowdStrike and Microsoft have released recovery tools and there have been reports of ‘significant recovery,’ as of today (23-July), Delta Airlines still announced the cancellation of 450 flights due to lingering effects.[10]
Malicious Activity and Domain Intelligence
We have come to expect that major news stories will spawn malicious cyber-attacks seeking to exploit the situation. Three leading cybersecurity companies – CrowdStrike (7/19), Flashpoint (7/19), SentinelOne (7-22) – have published open-source lists of malicious event-themed domains that are being reported as, or presumed to be, malicious. [3,7,8]
Before we received the feeds, we had set up our ‘Domain Intelligence’ projects in DomainTools using methods similar to those described in our most recent post, Bulletproof Hosting Havens for FIN7 and Russian Cyber Threat Groups. We loaded and tagged the CrowdStrike, Flashpoint, and SentinelOne feeds in DomainTools.
We also developed multiple Advanced Search queries for time-period (7 days and 1 day), risk level (80+ and none), and various word permutations. Methods and findings from our approach are shown in the following figures.
Figure 1 shows the Flashpoint and CrowdStrike sourced domains in DomainTools. Both were published on 7-19 with the Flashpoint collection consisting of 15 domains and the CrowdStrike collection consisting of 22 domains.
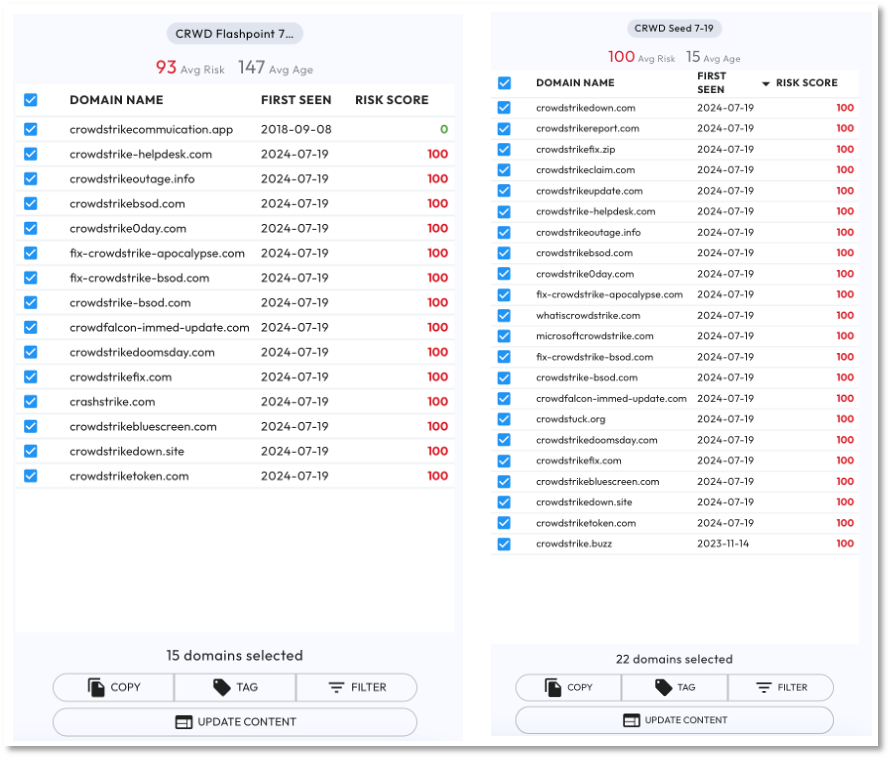
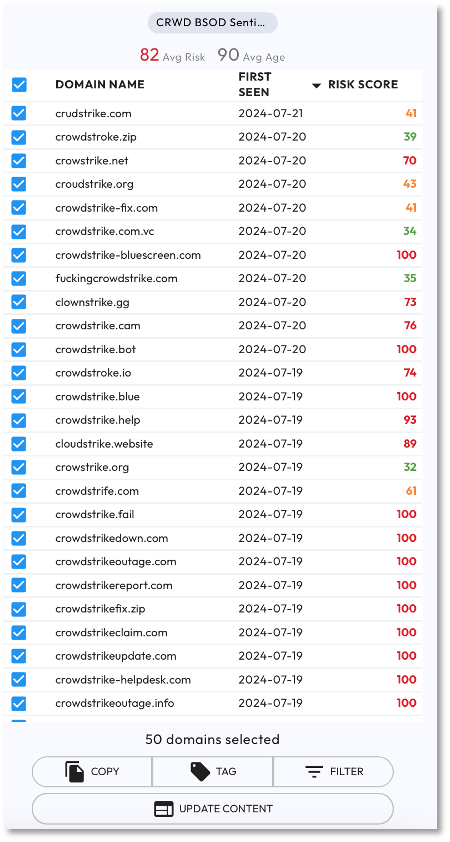
Figure 2 shows the SentinelOne sourced domains in DomainTools. This collection was published on 7-22 and consists of 50 domain names.
We also ran multiple Advanced Search queries in DomainTools to discover threats related to this incident independent of any ingested feed.
In Figure 3, we see a partial result of a DomainTools Advanced Search query (Boolean) we ran on 7-22 to discover new domain names:
- that were registered over the past 7 days AND,
- that have a high risk score (greater than or equal to 80) AND,
- that contain multiple thematically related words (OR statements),
- that resulted in 54 domains being added to the collection, after analyst review.
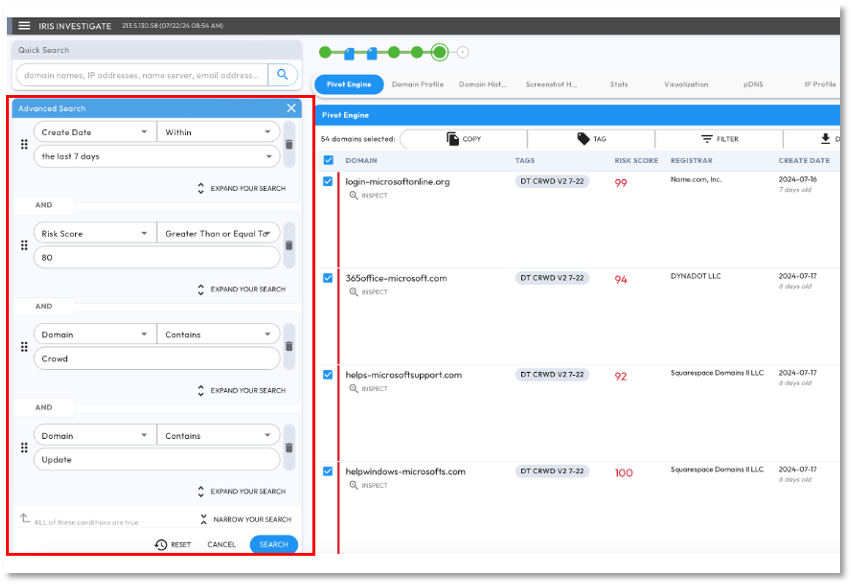
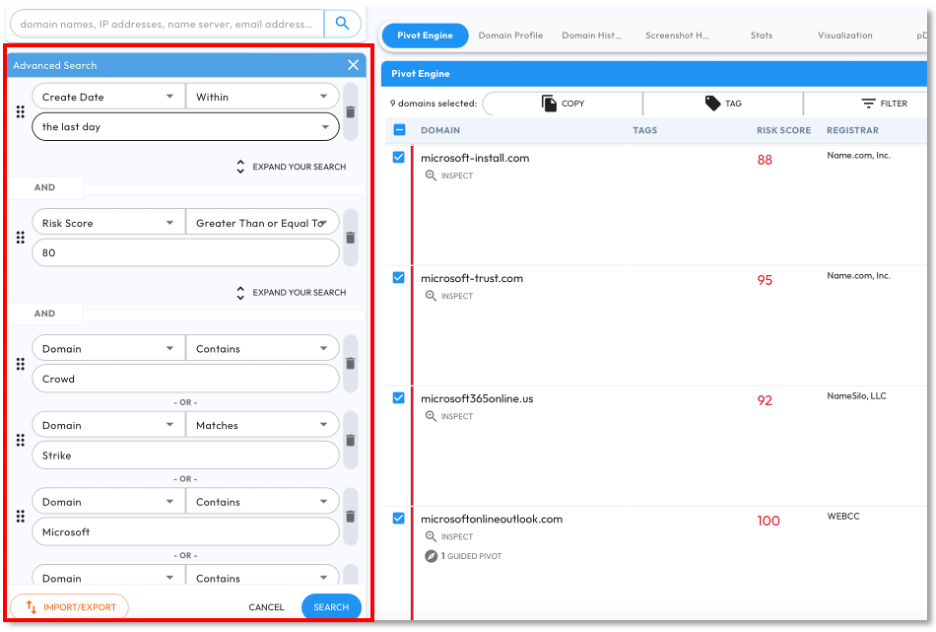
Figure 4 shows a partial result of a similar DomainTools Advanced Query we ran on 7-23 to discover new domain names that were registered:
- over the last day AND
- with a high-risk score (greater than or equal to 80) AND
- with multiple thematically related words (OR statements)
- that resulted in 9 domains being added to the collection, after analyst review.
GenAI Assistants
We also reviewed how we could use GenAI as an Analyst Assistant in this research. In Figure 5, we see GPT-4o prompts that use natural language to generate statistics and charts based on collections. See prompt and results.
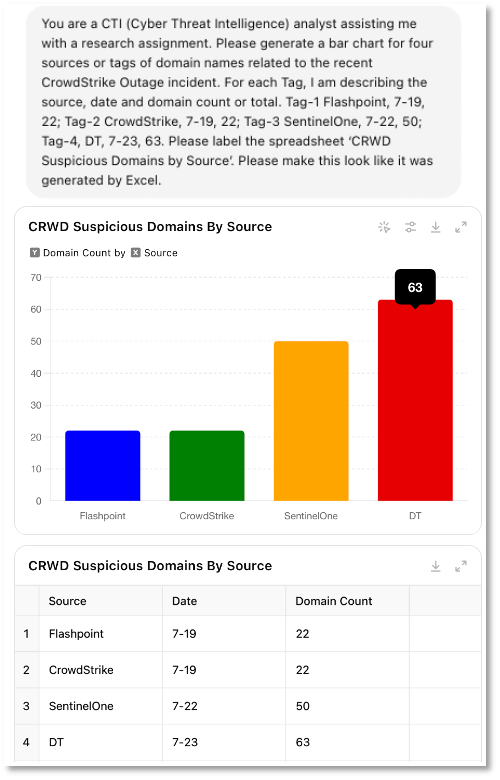
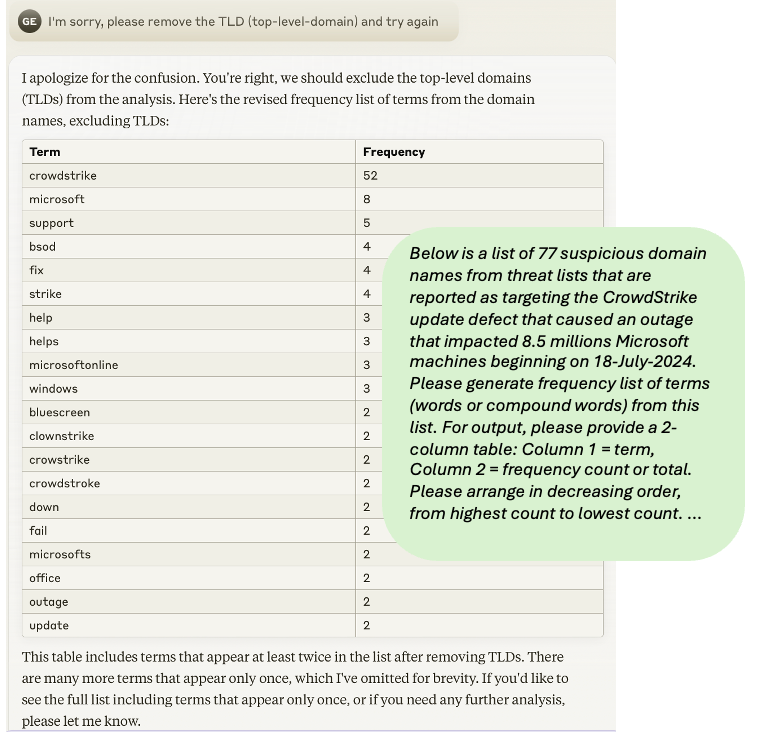
Figure 6 shows a prompt (green) and response from Anthropic’s Claude that generated a frequency distribution table of word form usage in the suspicious newly registered domains. Patterns learned from known malicious domains can be used to develop more effective advanced queries for discovering new suspicious domains.
Outlook
The techniques described above are proven methods for discovering domain threat intelligence. We will continue to apply these methods to monitor for changes in status and to discover new malicious domain names in this investigation.
References
- Microsoft – Helping our customers through the CrowdStrike outage , 20-July-2024
- Ars Technica – Microsoft says 8.5M systems hit by CrowdStrike BSOD, releases USB recovery tool , 22-July-2024
- SentinelOne – CrowdStrike Global Outage – Threat Actor Activity and Risk Mitigation Strategies , 22-July-2024
- Wired – Don’t Fall for CrowdStrike Outage Scams , 20-July-2024
- CrowdStrike – falcon-content-update-remediation-and-guidance-hub , 21-July-2024
- CrowdStrike – Falcon Sensor Content Issue from July 19, 2024, Likely Used to Target CrowdStrike Customers , 19-July-2024
- CrowdStrike – Likely eCrime Actor Uses Filenames Capitalizing on July 19, 2024, Falcon Sensor Content Issues in Operation Targeting LATAM-Based CrowdStrike Customers , 20-July-2024
- Flashpoint via LinkedIn , 19-July-2024
- NYTimes – What Happened to Digital Resilience?, 19-July-2024
- NYTimes – Transportation Department to Investigate Delta After Flight Delays , 23-July-2024
- Bleeping Computer – Fake CrowdStrike fixes target companies with malware, data wipers, 21-July-2024
- SC Media – Cyber Risk Alliance: Fallout from the CrowdStrike outage: Time to regulate EDR software , 22-July-2024
- TechCrunch – What we know about CrowdStrike’s update fail that’s causing global outages and travel chaos , 19-July-2024
