Recent reports from multiple trusted sources (CERT-UA, Microsoft Threat Intelligence, Lumen) published in December 2024, highlight ongoing Russian state-sponsored cyber espionage campaigns targeting Ukrainian drone operators and defense contractors. [1-4] The threat actors behind these attacks are tracked by multiple names including SVR, GRU, Secret Blizzard, Turla, Waterbug, Venomous Bear, UNC-4221, UAC-0185, and more.
Campaign Tactics, Techniques, and Procedures (TTP) include impersonating domains associated with Palantir, Microsoft, Google, WhatsApp, Signal, and Telegram. These platforms are considered high-value-targets (HVTs) due to their widespread use in secure communications, collaboration, and military applications, making them attractive for intelligence gathering and disruption efforts. Some of the campaigns had a clear focus on Starlink-connected devices and other critical systems.
Bottom Line: U.S. Defense Industrial Base (DIB) companies need to recognize that Russia’s interest in Ukraine’s defense technology signals a potential threat to U.S. contractors. Companies involved in drones, artificial intelligence, messaging, and communication systems are particularly at risk. To mitigate this, organizations should apply the hunting queries and indicators of attack (IOA) and preemptive threat indicators of future attack (IOFA) shared by threat researchers and ISACs (Information Sharing and Analysis Centers).
Campaigns Details
The campaigns reveal a strategic effort to compromise the technology infrastructure of Ukraine’s military capabilities and gain intelligence on operational tactics. Observed activities include:
- Phishing Campaigns: Threat actors launched spear-phishing campaigns leveraging domains impersonating major tech companies, such as Telegram, Signal, Microsoft, Google, Palantir, and Ivanti. The phishing emails contained malicious links or attachments designed to steal credentials or deliver malware.
- Infrastructure Exploitation: Adversaries targeted Starlink-connected devices, likely aiming to disrupt battlefield communications. Reports from CERT-UA indicated phishing pages mimicking legitimate services to harvest credentials.
- Impersonation of Trusted Platforms: Domains impersonating trusted communications, messaging, and drone systems were registered to exploit trust in popular platforms.
- Co-opting Cybercriminal Infrastructure: Secret Blizzard and Turla have appropriated infrastructure from other cybercrime groups to obscure attribution and expand operational reach.
These campaigns, which demonstrate changing and highly advanced TTPs designed to bypass traditional defenses, are a reminder of the need for vigilance and proactive measures among U.S. contractors.
Indicators
Indicators of Attack (IOA): Primary sources – including CERT-UA, Microsoft Threat Intelligence, and Lumen [1-4] – have shared hundreds of indicators of attack (IOAs) from multiple campaigns since 2022. These include domains, subdomains, URLs, IP addresses, email addresses, and malicious files. In this post our focus is on the domain name indicators. Preliminary lexical analysis of these indicators reveals the following product and platform targeting priorities:
- Telegram: 19 instances
- Microsoft: 8 instances
- WhatsApp: 3 instances
- Signal: 3 instances
- Google: 3 instances
- Palantir: 3 instances
- Ivanti: 1 instance
Indicators of Future Attacks (IOFA): With advanced DNS intelligence tools like Silent Push and DomainTools, cyber threat intelligence (CTI) teams can discover potential future attacks. By analyzing adversary TTP, new domain registrations, passive DNS records, and domain impersonations, organizations can identify threats before they are weaponized and preempt attacks.
To demonstrate this, we created a Newly Registered Domain (NRD) collection of 54 domain names that we built from searches in DomainTools and Silent Push. The searches looked for new domain name registrations (within 90) days with a high risk score (> 70) that matched lexical features contained in company names that corresponded to a non-random sample of U.S DIB companies. Our sample included both large traditional companies as well as innovative smaller companies providing drone and counter-drone systems. In Figure 1 we see a distribution of terms.
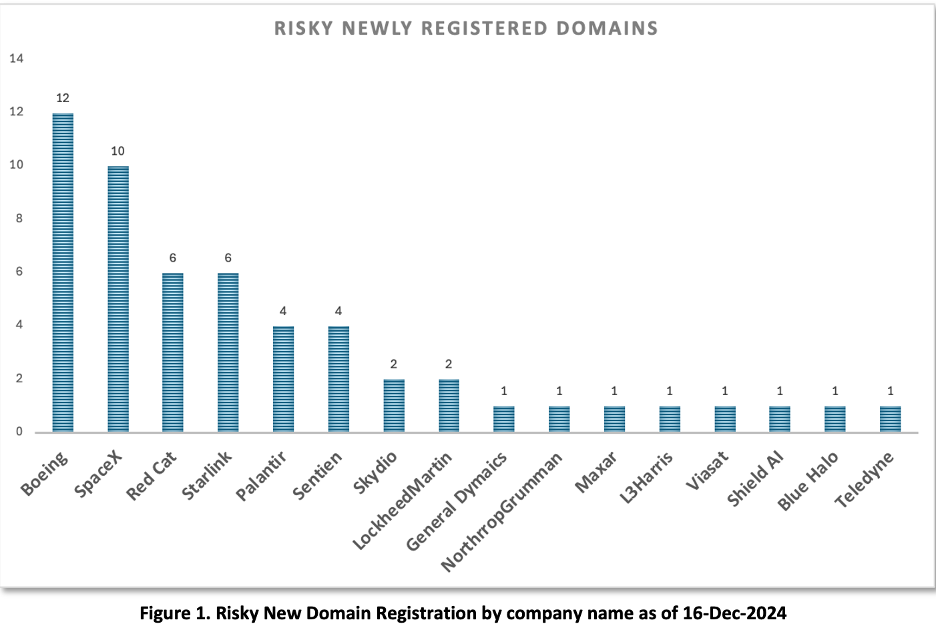
Recommendations
While the primary targets in the threat reports [1-4] are Ukrainian drone operators and defense contractors, the tactics present a possible spillover risk to U.S. DIB companies and warrant vigilant and proactive measures.
For comprehensive mitigation recommendations with mappings to the MITRE ATT&CK model and priority CVEs, see authoritative guidance in the Joint Cybersecurity Advisory [5] and CISA Cybersecurity Advisory [6]. With respect to our focus on phishing and DNS threats, DIB companies should:
1. Monitor for Domain Threats
- Continuously track threat actor infrastructure and domains related T1583.001 – Acquire Infrastructure: Domains (T1583.001).
- Implement passive DNS monitoring to identify brand impersonation for domains and subdomains, IP addresses and ranges, and infrastructure misuse. (MITRE ATT&CK T1596.001 – Search Open Technical Databases: DNS/Passive DNS)
2. Enhance Phishing Defenses
- Deploy advanced email security solutions to detect, block, and pre-empt spearphishing campaigns.
- Train employees to identify phishing attempts that impersonate leading DIB and technology companies, emphasizing signs of domain impersonation.
3. Strengthen Threat Sharing, Collaboration, and Incident Response
- Participate in ISACs and other sector-specific forums to share intelligence and defense strategies.
- Leverage shared threat intelligence from Information Sharing and Analysis Centers (ISACs) to stay updated on evolving TTPs.
- Develop and rehearse incident response plans to address domain impersonation, phishing attacks, and malware infections effectively.
4. Use Generative AI as a Research Assistant
- Generative AI (GenAI) tools can complement, augment, and enhance CTI research, reporting, translation, and training. For example, GenAI can assist in automating the analysis of multiple and large datasets to identify threat patterns, generating high-quality threat intelligence reports, translating technical documents, and simulating phishing scenarios for employee training. Our ThreatShare.ai Cyber Researcher chatbot, based on GPT-4, provides actionable insights to enhance analysis and decision-making as shown in Figure 2.
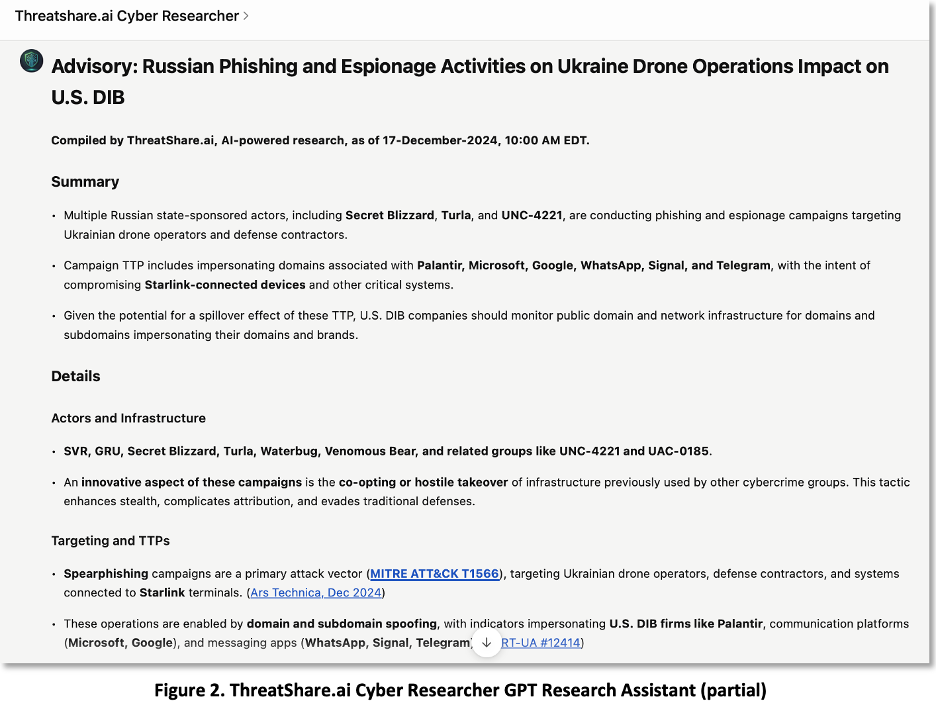
Editor’s Notes:
- Credit to our chatbots for their valuable assistance with threat analysis research, proofreading, and editorial review.
References
- CERT-UA – Targeted Cyberattacks by UAC-0185 on the Defense Forces and Defense Industry Enterprises of Ukraine (CERT-UA#12414) Published: 07.12.2024 Source: CERT-UA , 7-Dec-2024 https://cert.gov.ua/article/6281632
- Microsoft Threat Intelligence – Frequent freeloader part II: Russian actor Secret Blizzard using tools of other groups to attack Ukraine, 11-Dec-2024 , https://www.microsoft.com/en-us/security/blog/2024/12/11/frequent-freeloader-part-ii-russian-actor-secret-blizzard-using-tools-of-other-groups-to-attack-ukraine/
- Microsoft Threat Intelligence – Frequent freeloader part I: Secret Blizzard compromising Storm-0156 infrastructure for espionage, 4-Dec-2024 , https://www.microsoft.com/en-us/security/blog/2024/12/04/frequent-freeloader-part-i-secret-blizzard-compromising-storm-0156-infrastructure-for-espionage/
- Lumen – Snowblind: The Invisible Hand of Secret Blizzard, 4-Dec-2024 , https://blog.lumen.com/snowblind-the-invisible-hand-of-secret-blizzard/
- Joint Cybersecurity Advisory: Product ID: JCSA-20241010-001 – Update on SVR Cyber Operations and Vulnerability Exploitation, 10-Oct-2024, https://media.defense.gov/2024/Oct/09/2003562611/-1/-1/0/CSA-UPDATE-ON-SVR-CYBER-OPS.PDF
- CISA Cybersecurity Advisory: Alert CodeAA23-341A – Russian FSB Cyber Actor Star Blizzard Continues Worldwide Spearphishing Campaigns, 7-Dec-2023, https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-341a?utm_source=chatgpt.com
- MITRE ATT&CK: IDT1583.001 – Acquire Infrastructure: Domains
- Silent Push – https://explore.silentpush.com
- DomainTools Iris Investigate – https://www.domaintools.com/wp-content/uploads/DomainTools-Iris_Investigate_User_Guide.pdf
- Databricks – Detecting Criminals and Nation States through DNS Analytics , https://notebooks.databricks.com/notebooks/SEC/dns_analytics/index.html#dns_analytics_1.html
- Ars Technica – Russia takes unusual route to hack Starlink-connected devices in Ukraine, 11-Dec-2024 , https://arstechnica.com/security/2024/12/russia-takes-unusual-route-to-hack-starlink-connected-devices-in-ukraine/
- RecordedFuture – For Russian spies, existing cybercrime tools become avenues into Ukrainian military devices, 12-Dec-2024 , https://therecord.media/turla-secret-blizzard-russia-espionage-ukraine-cybercrime-tools
- DefenseNews – Top 100 Defense Companies for 2024 , https://people.defensenews.com/top-100/
