In this edition of our Sector Spotlight series, we review recent open-source research on cyber adversary and vulnerability intelligence relevant to the Waste and Water Sector (WWS), Communications, Electric Power, and Defense Industrial Base sectors. This report highlights practical applications of Generative AI (GenAI) tools as CTI assistants, particularly in conjunction with Shodan, as well as promising results from more complex searches using Perplexity’s newly released Deep Research product. The target audience for this report is cyber threat intelligence (CTI) professionals who support U.S. critical infrastructure sectors.
Industry experts have described critical infrastructure sector networks as being “in the crosshairs” of highly skilled and motivated cyber adversaries. [1, 2] These threat groups are multiplying, collaborating with each other, and persisting despite technical countermeasures, sanctions, and law enforcement actions. Their methods are both fundamental – exploiting well-known vulnerabilities – and innovative, leveraging GenAI to research targets and enhance operational effectiveness. They overwhelm defenders with attacks designed to deceive, distract, and exhaust cybersecurity teams.
In response, CTI providers and the media generate an immense volume of reporting on adversaries, attacks, vulnerabilities, tools, and methods. While this intelligence is necessary, it also results in a condition known as the ‘CTI paradox’ — where an overabundance of CTI, excessive focus on adversary-specific TTPs, and exhaustive CVE tracking can hinder rather than help cyber defense teams.
Effective defense strategies require a disciplined focus on cybersecurity fundamentals:
- Reducing the attack surface through network segmentation and access control.
- Securing identity by enforcing multi-factor authentication (MFA) and identity governance.
- Hardening ICS/OT environments by eliminating default credentials, securing remote access, and deploying robust monitoring solutions. [3]
Ultimately, proactive and resilient defensive strategies must be prioritized to counter the evolving threat landscape.
Threat Landscape: By The Numbers
Before considering recent reports on adversaries, vulnerabilities, and incidents, here is some context on the threat landscape. The following is a selection of authoritative sources we use to track cyber threat groups, their tactics, techniques, and procedures (TTPs), and related incidents. This list does not include numerous blog posts and premium CTI feeds provided by cybersecurity organizations that conduct primary research or share intelligence freely on platforms such as GitHub. Below are statistics from these sources as of February 15, 2025.
- MITRE ATT&CK: Source type – open; adversaries tracked – 163. [3]
- CrowdStrike: Source type – proprietary; adversaries tracked –245+. [4]
- malpedia: Source type – open; adversaries tracked – 800. [5]
- ThaiCERT: Source type – open; adversaries tracked – 495. [6]
The following summary from ThaiCERT provides a sense of the scope and scale of the threats facing CTI teams. The rapidly increasing volume of adversaries and attack methodologies presents significant challenges for cybersecurity teams.
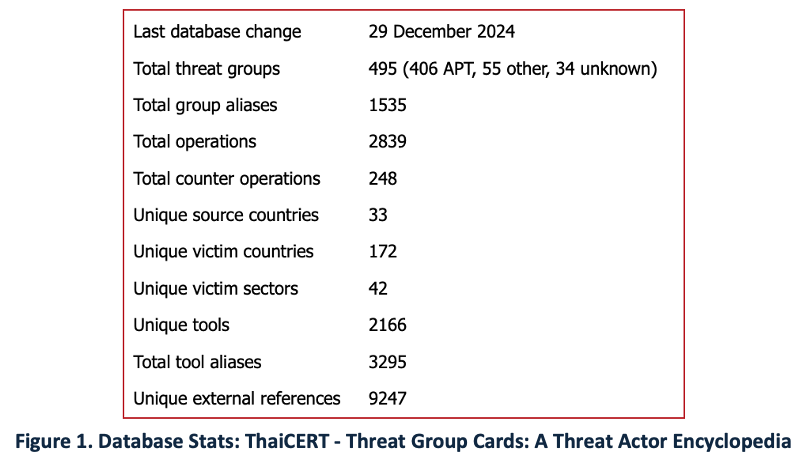
Beyond these sheer numbers, CTI and cybersecurity teams are expected to be subject matter experts (SMEs) on a large and expanding set of knowledge domains, including geopolitical, technical, business, legal, and societal factors. The rapidly evolving AI ecosystem introduces further complexity. It is not surprising that many teams struggle to keep pace.
Threat Landscape: Recent Reporting
In our previous post (23-Jan-2025) we reported 13 cyber-attacks against the IT and OT (Operational Technology) in the WWS sector in 9 states from 23-Nov-2023 to 22-April-2024, including attacks attributed to nation-state adversaries from China, Iran, and Russia. We also found that nearly 10% of organizations in the sector have critical or high-risk vulnerabilities.
Notable and Recent Adversary Group CTI
- While many CTI reports categorize threat groups by type (nation-state, APT, cybercriminal, hacktivist), research from the Google Threat Intelligence Group (GTIG 2-11-2025) and Trellix (1-14-2025) suggests that these distinctions may be arbitrary due to extensive collaboration among groups and the use of shared tools, methods, and infrastructure. [8, 9] Google notes that cybercrime groups outnumber state-backed groups by 4 to 1. Trellix finds that nation-state actors are more likely to target critical infrastructure sectors and governments, while criminal groups are more likely to target commercial organizations.
- Microsoft Threat Intelligence reports on the BadPilot campaign (2-12-2025) conducted by the Russian Seashell Blizzard subgroup, linked to the GRU. [11] The campaign exploits vulnerabilities in ConnectWise ScreenConnect (CVE-2024-1709) and Fortinet FortiClient (CVE-2023-48788), targeting critical infrastructure sectors including energy, water, government, military, transportation, and telecommunications.
- Recorded Future (Insikt Group) reports on persistent and ongoing campaigns targeting telecommunications providers by the Chinese nation-state actor commonly known as Salt Typhoon but tracked by Recorded Future as RedMike (2-13-2025). [12] The group is exploiting CVE-2023-20198 and CVE-2023-20273 to compromise unpatched Cisco IOS XE software. This campaign suggests that Salt Typhoon is undeterred by U.S. actions which include sanctions and multiple notices and advisories. [13-14]
- Another Google-GTIG report on Adversarial Misuse of Generative AI (1-29-2025) details the use of generative AI by more than 40 state-sponsored cyber adversary groups, including close to 20 by China and 10 from Iran. While AI is used across all attack phases, it is particularly effective in reconnaissance, delivery, weaponization, and command-and-control (C2). China’s use of GenAI to analyze public databases, open-source intelligence, and Shodan data for identifying targets could serve as a model for cyber defenders.
Vulnerability Advisories and Alerts
Just as cyber threat groups monitor vulnerability intelligence, so too must cyber defenders.. CISA’s Known Exploited Vulnerability Catalog (AKA KEV List) provides a searchable list of vulnerabilities that defenders can use to prioritize their vulnerability management plan. [34]
In our previous post we noted 30 CISA Advisories and Alerts data for 2024 relevant to the ‘Water and Wastewater Systems sector’. In addition, here’s an updated list of vulnerability categories and advisories we are tracking [14-31]:
- Exposed OT technologies (PLCs, HMIs, IoT, SCADA, ICS)
- Network devices (VPNs, firewalls, routers)
- Remote access tools and IT management software
Defenders should also develop their own intelligence collections to support their proactive threat hunting efforts, using resources such as:
- Shodan or Censys for passive vulnerability intelligence.
- Network and domain intelligence tools such as Silent Push for proactive measures.
- Dark web forums to monitor data leak sites, compromised credentials, and adversary chatter.
- Generative AI to enhance research, classification, and analysis capabilities.
Use cases
This section presents three use cases illustrating how CTI teams in critical infrastructure sectors can use Shodan and GenAI to augment and enhance their capabilities.
BadPilot Sector Risk
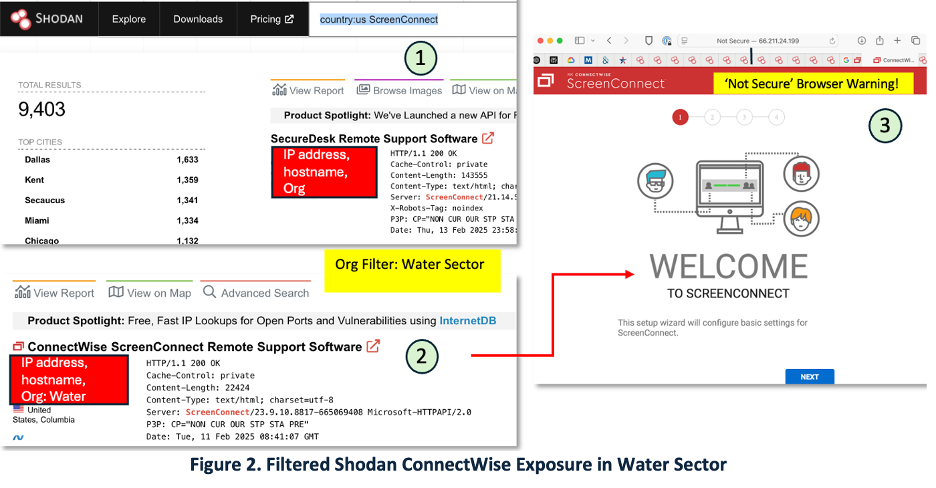
This simple use-case shows how a junior CTI analyst could use Shodan to assess whether a particular threat may be relevant to their network. Microsoft’s BadPilot 2-12-2025 report describes a campaign by a Russian state-sponsored group (Seashell Blizzard) targeting vulnerabilities in ConnectWise ScreenConnect (CVE-2024-1709) and Fortinet FortiClient (CVE-2023-48788). In Panel 1 of Figure 2, we see Shodan results from 2-12-2025 showing over 9,400 results of ConnectWise ScreenConnect systems in the U.S. From this screen the analyst could use ‘organization filters’ to discover devices in the WWS or other critical infrastructure sectors. In Panel 2, we see redacted results from a Water Sector systems that may be vulnerable. Panel 3 shows a ‘ browser warning’.
Exposed OT Devices
This is a complex use case for a senior CTI analyst working for a MSSP (Managed Security Services Provider) with customers in the communications, water, energy, and defense and government sectors. In this scenario, the senior analyst receives an RFI from their risk management team to assess the organization’s risk of PLC (Programmable Logic Controllers) devices exposed to the public Internet. The company has Allen-Bradley PLC devices from Rockwell Automation. The RFI was issued in response to threat advisories and alerts from EPA and CISA in December 2024. [16-17]
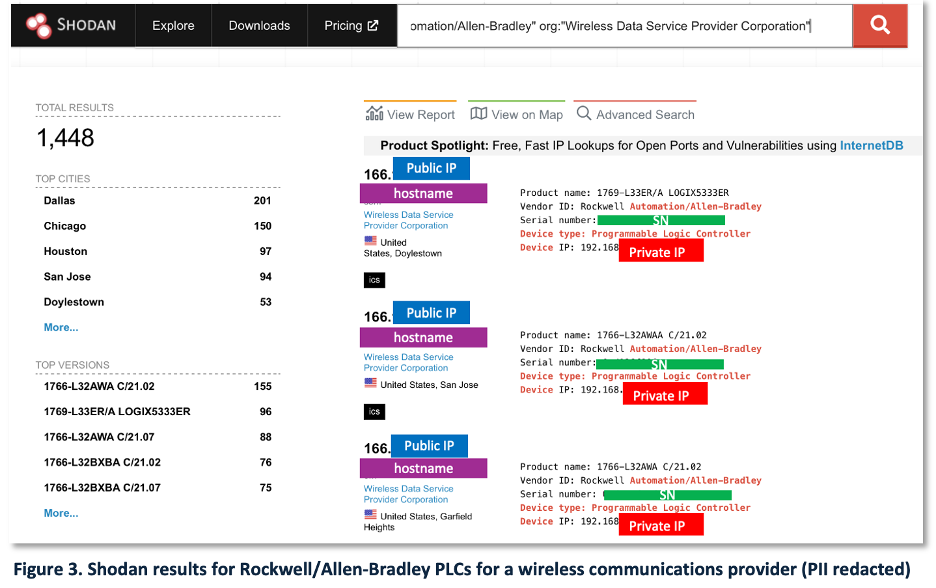
Shodan queries for ‘Allen-Bradley’ products reveal a concentration of exposed devices in Verizon networks, necessitating further investigation. Using GenAI as an assistant (ThreatShare Cyber Researcher via ChatGPT-4o), the analyst discovers potential segmentation issues.
Figure 3 shows redacted Shodan results. The analyst noticed a pattern in the metadata. For each hostname record there was a public IPv4 address displayed on the top left, and a private IP address in the bottom right. This is unusual. The analyst recalled seeing this in the past as a potential data leak from a network segmentation issue but wanted to escalate for an expert opinion.
As technical resources are tight, the analyst used GenAI as an assistant. After several iterations, the analyst submitted a complex prompt to the GenAI. Partial results from the GenAI (ThreatShare Cyber Researcher implementation of ChatGPT 4o) are shown in Figure 4. The following summary from the GPT Assistant confirms the analyst’s network security concerns:
“A. Private IP Address Leakage
• The presence of both public and private IPs in the Shodan results suggests misconfigured network address translation (NAT) or improper exposure of internal device details.
• RFC 1918 private addresses (e.g., 192.168.x.x, 10.x.x.x) should be strictly internal and never visible via public scans. Leaking these addresses could help attackers identify network topology.
• Hurricane Electric BGP Toolkit shows Verizon announcing bogon IPs, meaning private IP addresses may be incorrectly advertised over Border Gateway Protocol (BGP), exposing internal network details.”
While more verification is warranted, preliminary review suggests the GenAI assessment is reasonable

Perplexity Deep Research
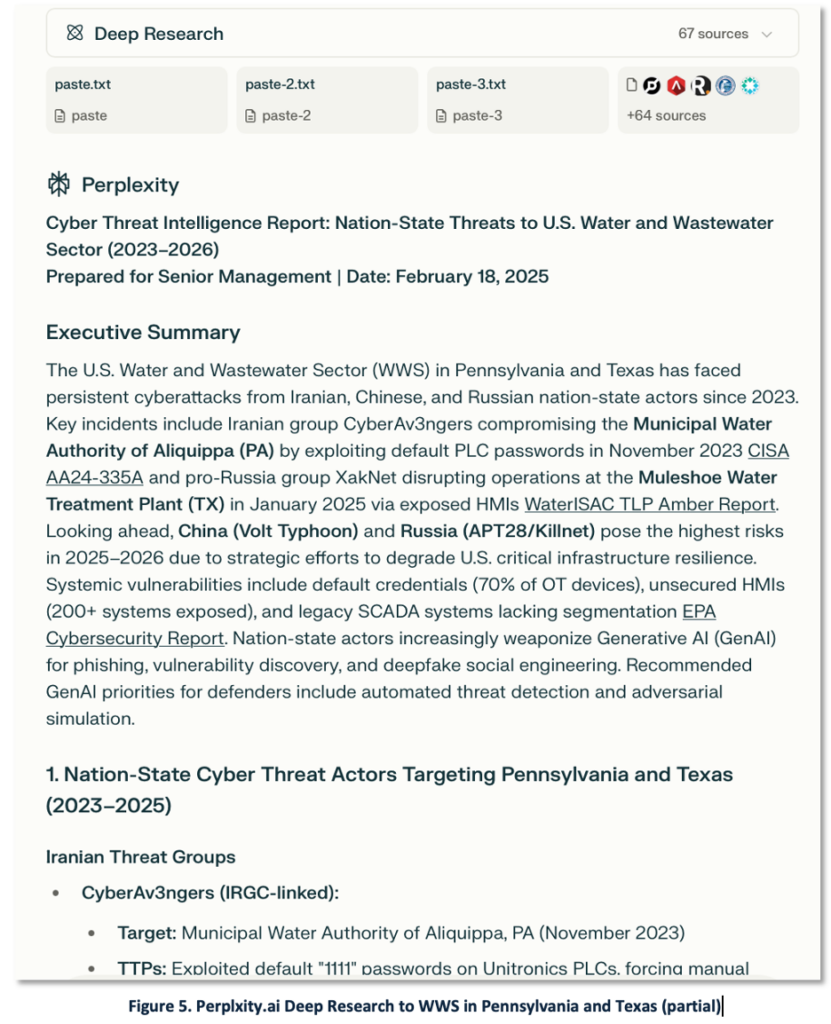
This is another example of a complex request for WWS intelligence. In this scenario, the CTI team received an RFI for a 3-page report with a 300 word executive summary of Cyber Threats to the WWS sectors in Pennsylvania and Texas. This seemed like a good opportunity to test Perplexity’s newly released Deep Research product. A preliminary but unverified assessment is favorable. The citation of 64 sources suggests a thorough analysis that facilitates analyst verification.
Outlook
The call to action for cyber defenders in critical infrastructures is clear: they must focus on the fundamentals and proactively and continuously monitor their IT and OT devices and networks, domain names and subdomains, accounts, and third-parties.
It is difficult to overstate the severity of the cyber threat to critical infrastructure sector networks. In recent testimony to the House Select Committee on the Chinese Communist Party, Former CISA Director Jen Easterly captured the Chinese cyber threat starkly, describing disruptive attacks in an: “Everything Everywhere, All at Once scenario … our transportation nodes, our telecommunications services, our power grids, our water facilities, and likely much more—all with the goal of inducing societal panic and deterring our ability to marshal military might and citizen will to expend American blood and treasure in defense of Taiwan.” [13].
Amid the hype around GenAI for cyber, it’s important to be pragmatic. GenAI is not magic. It is a tool that needs to be trained, closely supervised, and applied to improving cybersecurity fundamentals. Think of it as a promising new hire – one that sometimes disappoints but often exceeds expectations.
Our adversaries are already using GenAI to increase the frequency and sophistication of their cyberattacks. As we consider how the U.S. critical infrastructure cyber community should incorporate GenAI into its defenses, we are reminded of the TINA principle and acronym espoused by former British Prime Minister Margaret Thatcher: “There is no Alternative”. [33]
Editor’s Note:
- Acknowledgment to our chatbots for their valuable support in sector classification, name entity recognition and extraction, research, and editorial review.
References
- Barracuda – Water and wastewater systems in the crosshairs , 28-Feb-2024
- Forbes – Hacktivism On The Rise: Protecting Critical Infrastructure Is Top Priority, 3-June-2024
- Water-ISAC – 12 Cybersecurity Fundamentals for Water and Wastewater Utilities, December 2024
- MITRE ATT&K – Groups
- CrowdStrike – CrowdStrike 2024 Global Threat Report., 28-Feb-2024
- Fraunhofer FKIE – Malpedia database
- ETDA: Electronic Transactions Development Agency (AKA ThaiCERT) – Threat Group Cards: A Threat Actor Encyclopedia
- Google Threat Intelligence Group (GTIG) – Cybercrime: A Multifaceted National Security Threat, 11-Feb-2025
- Trellix – Blurring the Lines: How Nation-States and Organized Cybercriminals Are Becoming Alike, 14-Jan-2025
- Google Threat Intelligence Group (GTIG) – Adversarial Misuse of Generative AI, 29-Jan-2025
- Microsoft Threat Intelligence – The BadPilot campaign: Seashell Blizzard subgroup conducts multiyear global access operation, 12-Feb-2025
- Recorded Future (Insikt Group) – RedMike (Salt Typhoon) Exploits Vulnerable Cisco Devices of Global Telecommunications Providers, 13-Feb-2025
- CISA Blog – Strengthening America’s Resilience Against the PRC Cyber Threats, 15-Jan-2025
- CISA Enhanced Visibility and Hardening Guidance for Communications Infrastructure , 4-Dec-2024
- CISA – Guidance and Strategies to Protect Network Edge Devices, 4-Feb-2025
- CISA – EPA Advisory: Internet-Exposed HMIs Pose Cybersecurity Risks to Water and Wastewater Systems, 10-Dec-2024
- CISA: Cybersecurity Advisory, Alert Code AA24-335A – IRGC-Affiliated Cyber Actors Exploit PLCs in Multiple Sectors, Including US Water and Wastewater Systems Facilities, 18-Dec-2024
- Industrial Cyber – DHS warns Chinese-made internet cameras pose espionage threat to US critical infrastructure, 10-Feb-2025
- ReliaQuest Threat Landscape Report: Uncovering Critical Cyber Threats to Utilities , 10-Dec-2024
- Barracuda Networks – Infrastructure defense: Water and wastewater systems, 26-Dec-2024
- Barracuda Networks – Threat Spotlight: The remote desktop tools most targeted by attackers in the last year, 1-May-2024
- CISA, Alert CodeAA24-038A: PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure , Release Date: February 07, 2024
- CISA (FBI-DC3) Alert CodeAA24-241A – Iran-based Cyber Actors Enabling Ransomware Attacks on US Organizations, 28-Aug-2024
- CISA – Joint Advisory: Defending OT Operations Against Ongoing Pro-Russia Hacktivist Activity, 1-May-2024
- CISA – CISA Mitigation Instructions for CVE-2025-0282 (Ivanti Connect Secure)
- CISA: Cybersecurity Advisory, Alert Code AA24-038A – PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure, 7-Feb-2024
- Ivanti – Security Advisory Ivanti Connect Secure, Policy Secure & ZTA Gateways (CVE-2025-0282, CVE-2025-0283), Created 8-Jan-2025, Update 21-Jan-2025
- Water-ISAC – Cyber Resilience – Cybersecurity Challenges Facing Water Utilities , 2-Jan-2025
- WaterISAC – TLP Amber Report: Threat Analysis for Water and Wastewater Sector, 30-Sept-2024
- Palo Alto Network – Unit 42: Threat Brief: CVE-2025-0282 and CVE-2025-0283 (Updated Jan. 17) , 17-Jan-2025
- Censys – January 10 Advisory: Actively Exploited Unauthenticated RCE in Ivanti Connect Secure [CVE-2025-0282], update 13-Jan-2025
- Perplexity.ai – Introducing Perplexity Deep Research, 14-Feb-2025
- The Guardian – If the AI Roundheads go to war with tech royalty, don’t bet against them, 15-Feb-2025
- CISA (KEV Catalog) – Known Exploited Vulnerabilities Catalog
