Initially, this post was intended to be a routine review of how cyber threat actors utilize domain names and DNS infrastructure, how these uses evolve, and how cyber threat analysts can use DNS intelligence to counter threat actor operations. Kudos to Silent Push for inspiring this post with their excellent report and data on the Russian-linked threat actor, FIN7. [1]
However, as is often the case with cyber investigations, when we dig deeper things get more complex. And interesting. Our analysis of the domain names and DNS infrastructure associated with FIN7 attacks revealed a transnational network of bulletproof hosters. These hosters support a wide range of malicious activity including phishing and ransomware attacks by Russian cybercriminal groups, DDoS campaigns by hacktivist groups, and disinformation campaigns conducted by Russia’s GRU military intelligence service dating back to the 2008 Russian invasion of Georgia. Special thanks to KrebsonSecurity and CORRECTIV, a German collective of investigative journalists, for their reporting on bulletproof hosters. [5-7]
In addition to Silent Push and other authoritative CTI sources, our research was enabled by the DomainTools Iris platform for DNS intelligence, and a suite of GenAI research assistants.
In this post we:
- Provide a comparative review of a selected sample of domain names and DNS infrastructure used in FIN7 campaigns from 2022 to July 2024.
- Provide examples of proactive DNS threat hunting techniques in one of the bulletproof hosting networks used by FIN7.
- Review bulletproof hosters supporting FIN7 and Russian hybrid warfare operations.
- Introduce new applications of GenAI for DNS Intelligence investigations.
- Assess the current threat posed by bulletproof hosters and offer recommendations for cyber defenders.
Bottom line: FIN7 is a skilled and resilient Russian-linked cybercrime group that has been in business since 2013. Despite takedowns, sanctions, and arrests, they remain an active threat. They are sustained by a complex and opaque network of bulletproof hosters. These hosters, which derive income from Russian-linked cybercriminal and nation-state actors, operate with apparent impunity across multiple jurisdictions including Russia, Moldova, the Netherlands, Cyprus, the U.S., and others. Advanced and proactive DNS methods and tools can help cyber defenders counter bulletproof hosters and cyber threat groups, as can more aggressive and coordinated international enforcement and sanctions.
Notes on Scope:
- The sourcing from Silent Push is limited to the network indicators (domains and IP addresses) available through the ‘community edition’ report. Silent Push also provides a TLP:Amber version with thousands of indicators for enterprise customers.
- The scope of our analysis is limited to network indicators related to domain name registration and hosting. Actor motivations, TTPs (tactics, techniques, and procedures), tools, and malware are beyond this scope.
FIN7 DNS Comparison
When we read Silent Push’s July-10 report on the domain infrastructure used in recent FIN7 campaigns [1], it seemed like a good opportunity to compare this campaign to previous FIN7 campaigns reported from other opensource CTI (Cyber Threat Intelligence) reports. So, we created two collections: Collection 1 contains 68 mostly recent domain names from the Silent Push report (community edition), while Collection 2 includes 79 older indicators drawn from reports by Mandiant, Microsoft, and eSentire.
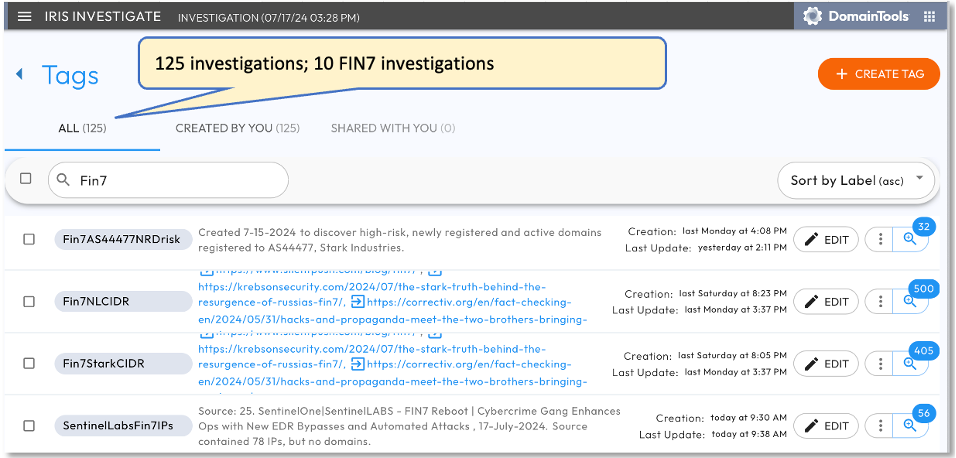
On May 11, we uploaded the May 10 Silent Push indicators into DomainTools, adding it to our existing repository of 125 investigations developed over five years. This repository includes ten investigations associated with FIN7. (Figure 1)
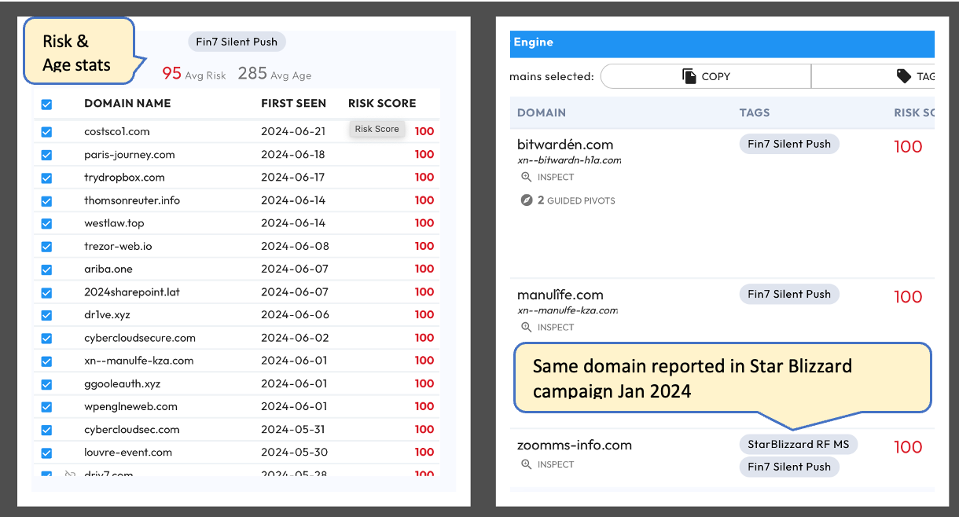
On the left panel in Figure 2 we see a partial view in DomainTools of the domains sourced from Silent Push. Note the ‘First Seen’ date (column 2) shows most of the domains are newly registered since 30-May and have a high DomainTools risk score (column 3). In the right panel, note that only one of the domains in the Silent Push collection was previously seen in the ‘Star Blizzard’ collection from Microsoft in January 2024.
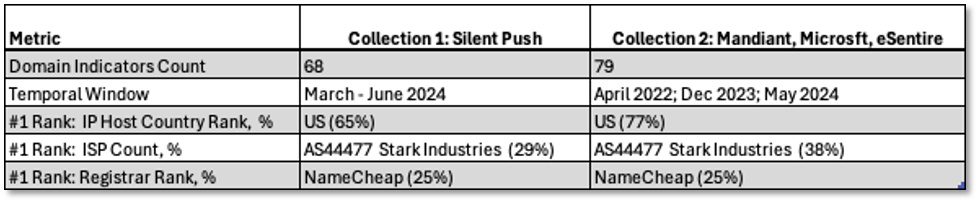
Observations and insights from our comparative summary in Table 1:
- These collections are small and similar in size, suggesting targeted operations.
- The collections have different temporal windows.
- The domains are predominantly hosted in the U.S., which, while potentially reducing the likelihood of being blocked, also exposes FIN7 to U.S. law enforcement actions.
- Stark Industries (AS44477) and NameCheap are the preferred providers of hosting and domain registration services in both collections, suggesting established business relationships with infrastructure providers known for lax oversight.
While we cover GenAI applications for DNS Intelligence later in this post, it’s worth noting here how an analyst could use GenAI to interpret data. We fed the comparative data for both collections as a CSV to our chatbot suite (GPT-4, GPT-4o, Perlexity.ai, and Claude from Anthropic) and asked them to assist. As shown in Figure 3, Perplexity.ai’s conclusions are reasonable and usable, provided they are reviewed by a human analyst.

Proactive DNS Threat Discovery
In the previous examples, we demonstrated a descriptive analytics use-case, where we used DomainTools to aggregate and enrich data that was previously discovered from other intelligence sources. As we know from our experience as CTI analysts and from our GPT-4o research assistant, descriptive analytics ‘lays the groundwork for more advanced analytics like predictive and prescriptive analytics’.
Proactive DNS threat discovery techniques from leading DNS Intelligence solution providers like Infoblox, Palo Alto Networks, and DomainTools have proven to be effective. [9] In this section we provide two examples of how analysts can use DNS Intelligence to proactively to discover or hunt potential threats before they are weaponized.
Proactive DNS threat discovery techniques from leading DNS Intelligence solution providers like Infoblox, Palo Alto Networks, and DomainTools have proven to be effective in identifying potential threats before they are weaponized. [9] This section describes two methods of using DNS Intelligence to proactively discover or hunt potential threats.
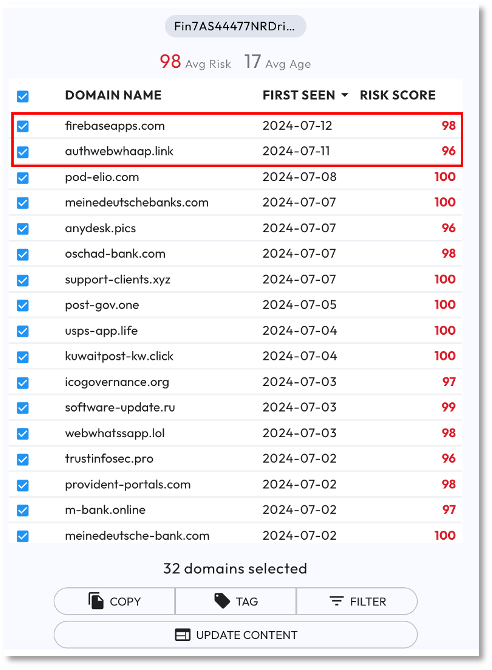
As noted by Silent Push, KrebsonSecurity, and COMPARTI, Stark Industries Solutions (AS44477) is a notorious bulletproof hoster linked to FIN7 and many other criminal, hacktivist and nation-state threat actors. On July 15, we created a proactive investigation in DomainTools for the purpose of discovering: active, high-risk (score > 80), and newly registered (within 30-days) hosted by AS44477 Stark Industries.
In Figure 4 we see that this query generated 32 domains with an average risk of 98 and age of 17 days. As highlighted, we see two domains targeting Google and Meta with high risk scores that were registered after the Silent Push report but have not yet been reported in campaigns.
Another proactive method involves using pDNS (passive DNS) on specified domains, IP addresses, or CIDR blocks. As shown in Figure 5, we selected a Stark Industries CIDR (103[.]35.191.0/24) which generated 5,000 DNS records of domains and subdomains resolving to IPs in this range. A closer examination of these records revealed that many of these domains, identified between July 12-15, were newly registered domains and have high risk scores.
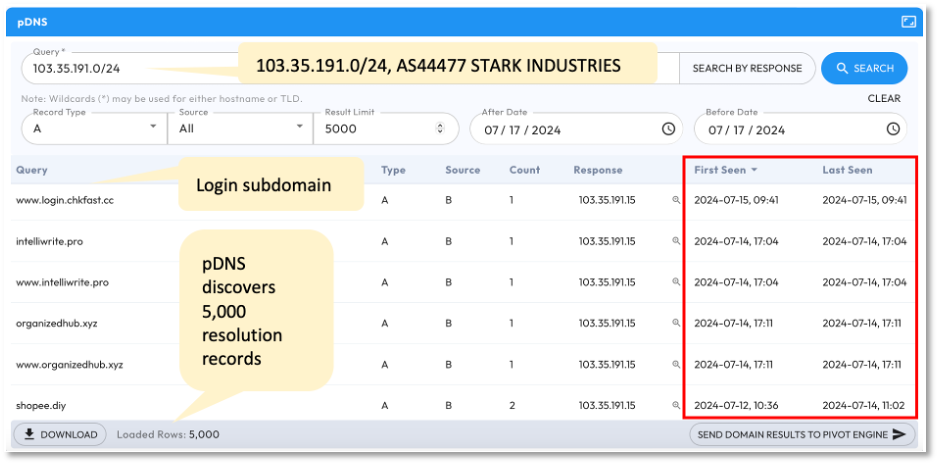
Intelligence derived with proactive DNS can be automated and integrated with cybersecurity solutions such as Web Proxies, Web Application Firewalls, and Endpoint Detection and Response (EDR) systems to block communications with suspicious domains.
DNS in Bulletproof Hosting
Silent Push identified the prominent role of bulletproof hosters such as Stark Industries in their report. Krebs and COMPARTIV expanded on this topic with details on:
- The scale of the transnational bulletproof operators (spanning 20 Autonomous Systems, thousands of IP ranges and proxy networks representing over a million IP addresses);
- The principals behind these networks, specifically the Neculiti brothers, Ivan and Yuri, from Moldova.
- The variety of threat actors utilizing these bulletproof networks, including criminal groups like FIN7, pro-Russian hacktivists ((NoName057(16)), and Russian state-sponsored entities (Sandworm, GRU).
- Prominent campaigns involving phishing, DDoS, Disinformation (Doppelganger), destructive wiper attacks.
- Geopolitical targeting spanning Ukraine, Moldova, the French elections, Germany, the US, and other Western EU countries.
To get a sense of the infrastructure scale, we explored the Autonomous System Numbers (ASNs) that are the backbone for routing and the domain name to IP resolution. Using BGP (Border Gateway Protocol) Observability Tools like Hurricane Electric BGP Toolkit , Cloudflare Radar – Routing , BigDataCloud – AS44477 , IPinfo AS44477 , Kentik Network Observability Platform), we captured essential routing metrics as detailed in Table 2.
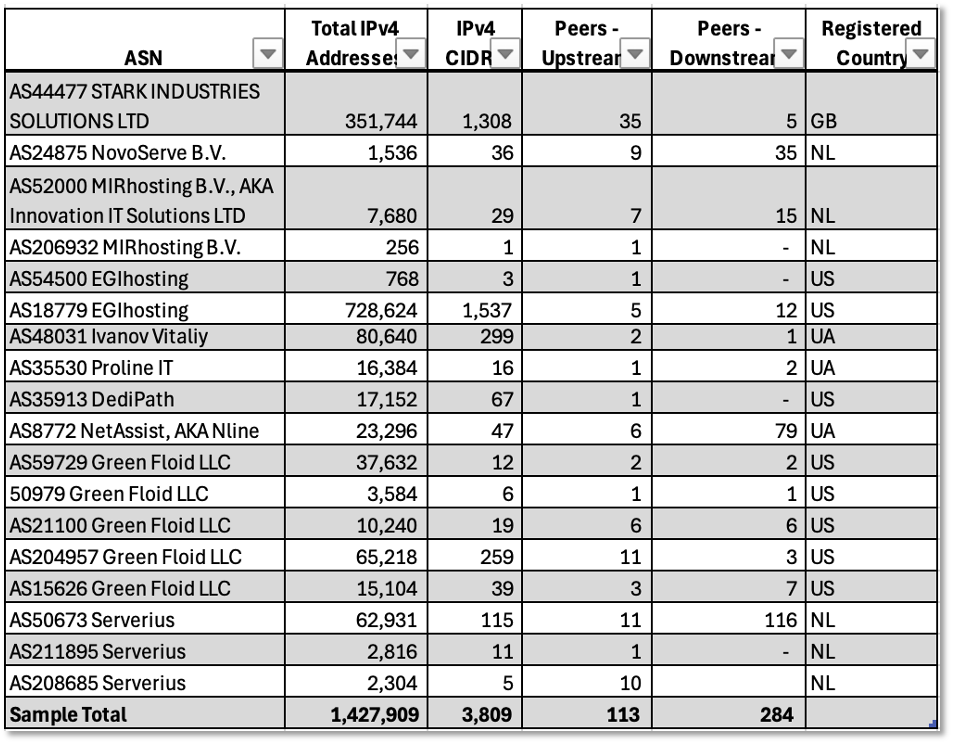
Armed with this knowledge of ASNs, CTI analysts use DomainTools Advanced Search functions for AS-specific and passive DNS (pDNS) searches to proactively identify domain threats, as discussed in the previous section. Knowledge of peering relationships can also enable cyber defenders, governments, and law enforcement to discover problematic relationships with bulletproof hosters. For example, of the five ASNs that are downstream from Stark Industries, 2 are registered in Russia, with 1 each in the U.S., Great Britain and Cyprus. Peering intelligence can also be used to identify routing related risks, such as BGP hijacking, route leaks, and RPKI (Resource Public Key Infrastructure) status.
GenAI for DNS Intelligence
DNS and Domain Name Intelligence are essential but specialized skills within the broader field of Cyber Threat Intelligence (CTI). While many CTI analysts have a basic understanding of DNS, in-depth expertise is less common. This disparity presents an excellent opportunity for managers to use Generative AI (GenAI) to ‘upskill’ less-experienced CTI analysts. Below are two use cases where we used GenAI to enhance our CTI analysis and reporting.
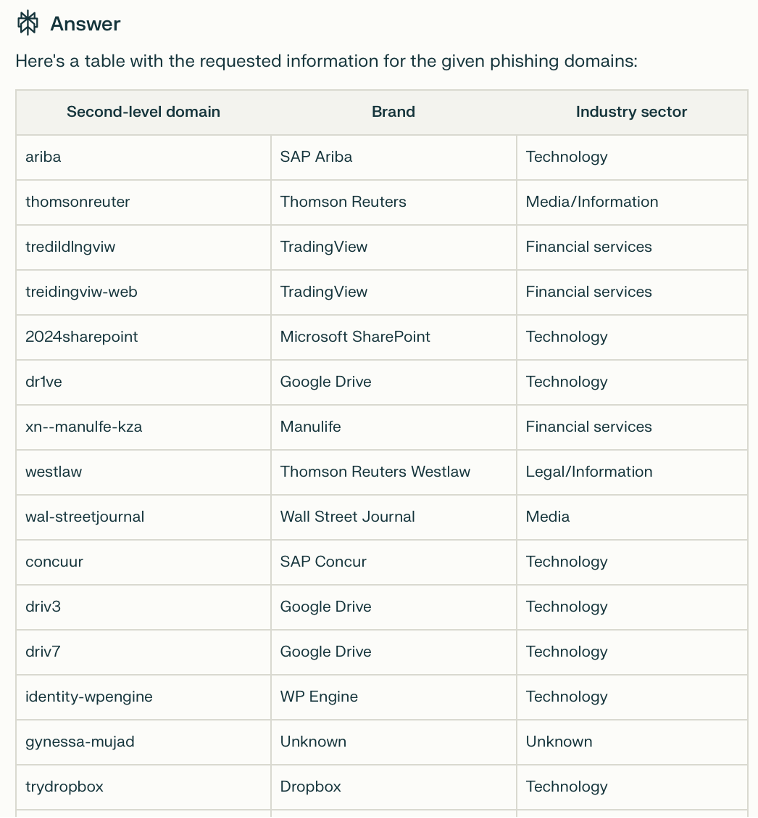
Use-case 1: An analyst needs to review 140 unique domain names aggregated from reports by Silent Push, Mandiant, Microsoft, and eSentire. Often this may involve examining various name permutations for potential phishing threats using DNS fuzzing tools like dnstwist. GenAI can help simplify this process. For example, we used GenAI to classify phishing domains by brand and industry sector, simplifying what would otherwise be a complex and time-consuming task. Figure 6 shows the prompt we created for our chatbot suite, while Figure 7 shows results generated by Perplexity.ai.

Use-case 2: For our second use-case, refer back to Collection 2 as shown in Table 1. Generating graphics for reports and dashboards is a common CTI analyst task. This can sometimes be a complex task with tools like Excel, Splunk, Tableau, Sigma, etc. Another approach would be for the CTI analyst to simply describe what they want in natural language, as shown in Figure 8. In this example we want to take a subset of a spreadsheet generated by DomainTools, upload the CSV to GPT-4o and ask it to generate one trend-line, one pie chart, and two bar chart that could be plugged into a report or dashboard as shown in Figures 9 – 14.
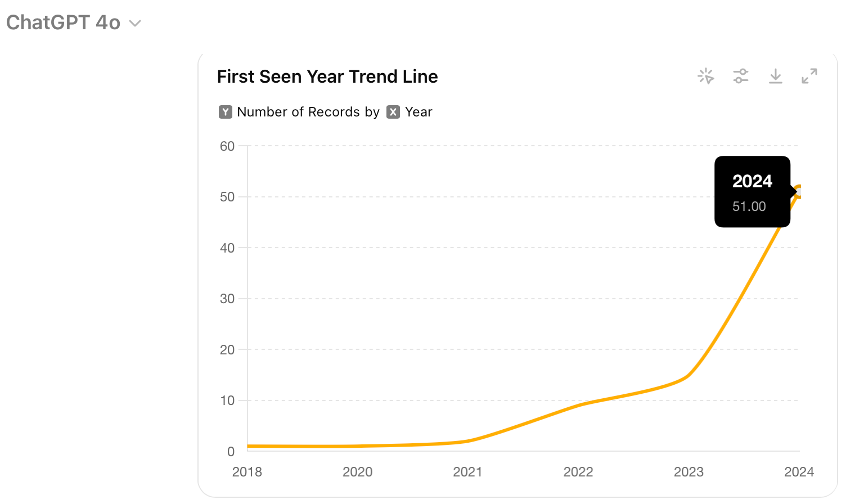
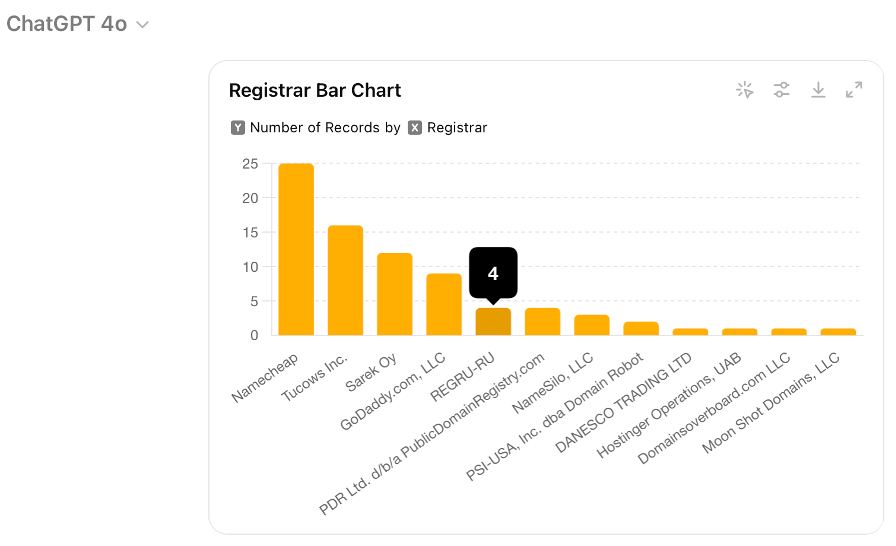
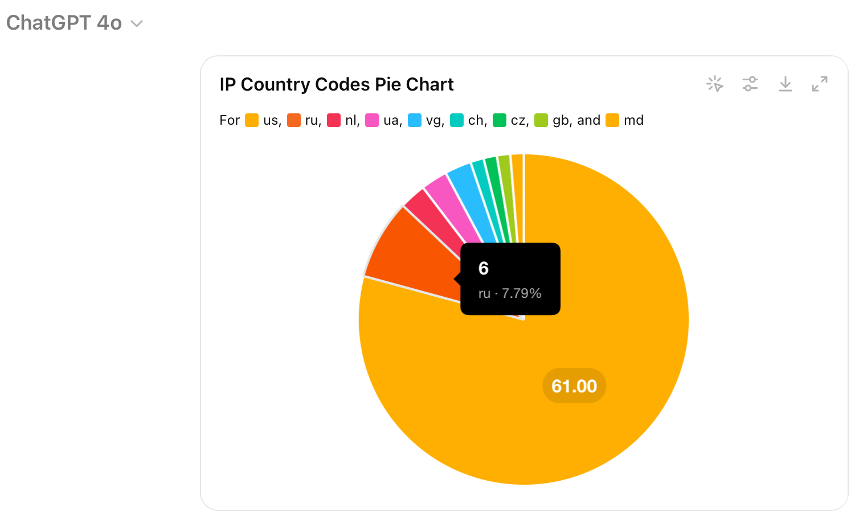
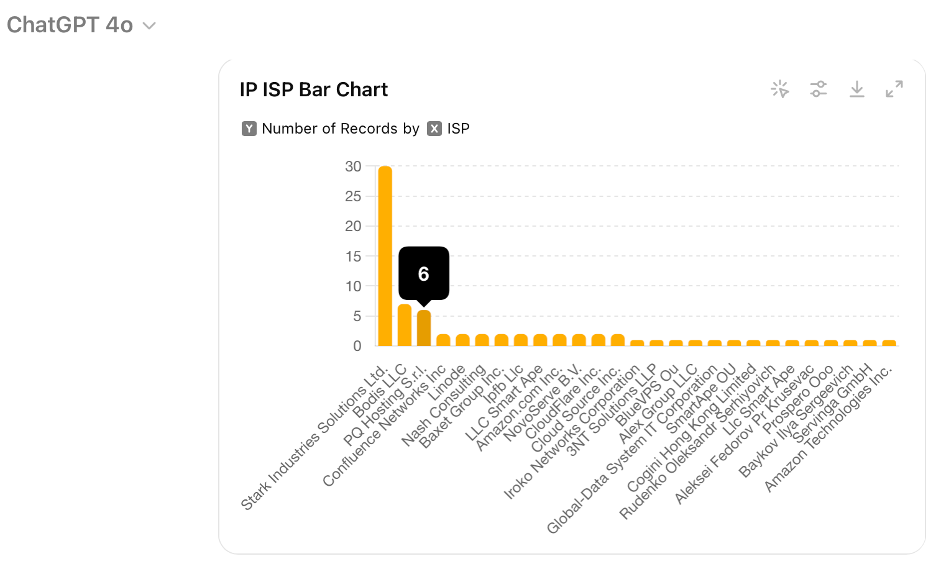
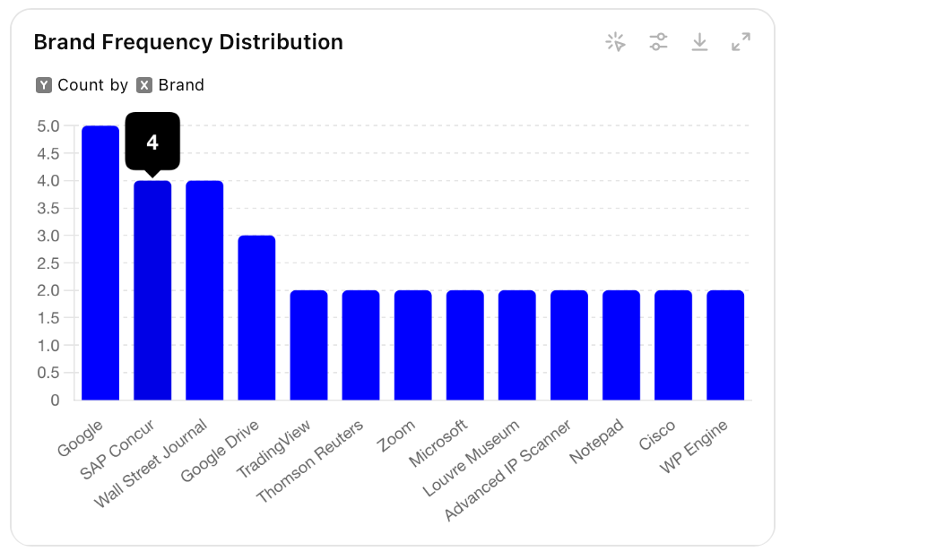
With applications like these, GenAI has the potential to be a transformative tool for DNS intelligence, enabling analysts to perform higher-level tasks and contribute more strategically to cyber defense efforts. At the same time, it is important to recognize that developing effective prompts for CTI is a learned skill that takes time and experience. It is also important to understand the types of prompts that are not likely to be effective.
Recap and Outlook
Russian nations-state actors, hacktivists and cyber criminals use bulletproof hosters services to facilitate a range of malicious activities, including phishing, brand impersonation, fraud, ransomware attacks, DDoS, destructive wiper attacks, and disinformation campaigns. These operations have intensified since the 2008 Russian invasion of Georgia. Despite arrests, FIN7 remains a formidable force. The SentinelLABS threat recent report dated 17-July-2024 shows that FIN7 is still active. [17]
Faced with these challenges, more proactive cyber defenses are needed. The data sources and methods are known. APIs are from leading DNS Intelligence providers like Infoblox, Palo Alto Networks, DomainTools, and Silent Push are effective solutions that can work at scale. Adversaries are using GenAI for targeting, and to improve the effectiveness and frequency of their attacks. Cyber defenders must counter these GenAI-enabled threats with GenAI enabled defenses.
Finally, aggressive takedowns, sanctions, and law-enforcement actions are needed to inflict higher costs on the bulletproof hosters. Stronger actions against domain registrars that profit from the sale of domains that fuel these phishing and disinformation attacks are a good starting point. EU sanctions against the bulletproof hosters have been called ‘toothless’ [7]. Our searches of the U.S. Department of Treasury’s SDN-OFAC database did not yield any results. This indicates a clear need for more aggressive sanctions designations and enforcement against these malign actors.
Editor’s Notes:
- Credit to ChatGPT, Perplexity, and Claude for valuable assistance with threat analysis research and proofreading.
- The Featured Image for this blog is a human-created mashup sparked by inspiration from CORRECTIV, iZOOlogic, and EUvsDisinfo.
References
- Silent Push – FIN7: Silent Push unearths the largest group of FIN7 domains ever discovered. 4000+ IOFA domains and IPs found. Louvre, Meta, and Reuters targeted in massive global phishing and malware campaigns. , 10-July-2024
- Mandiant – FIN7 Power Hour: Adversary Archaeology and the Evolution of FIN7 , 4-April-2022
- Microsoft Threat Intelligence – Financially motivated threat actors misusing App Installer, 28-Dec-2023
- eSentire – FIN7 Uses Trusted Brands and Sponsored Google Ads to Distribute MSIX Payloads , 8-May-2024
- KrebsonSecurity – The Stark Truth Behind the Resurgence of Russia’s FIN7 , 10-July-2024
- KrebsonSecurity – Stark Industries Solutions: An Iron Hammer in the Cloud , 23-May-2024
- CORRECTIV – Hacks and Propaganda: Meet the Two Brothers Bringing Russia’s Cyber War to Europe, 31-May-2024
- SentinelOne|SentinelLABS – FIN7 Reboot | Cybercrime Gang Enhances Ops with New EDR Bypasses and Automated Attacks , 17-July-2024
- Infoblox – BREAK THE RANSOMWARE SUPPLY CHAIN WITH DNS THREAT INTEL , 31-May-2024
- U.S. DOJ – Team from Western Washington honored for investigation and prosecution of major cybercrime group FIN7 , 3-May-2023
- Hurricane Electric – BGP Toolkit. https://bgp.he.net/AS44477
- Cloudflare Radar – https://radar.cloudflare.com/routing/as44477
- MITRE ATT&CK – FIN7
- Esentire – Notorious Cybercrime Gang, FIN7, Lands Malware in Law Firm Using Fake Legal Complaint Against Jack Daniels’ Owner, Brown-Forman Inc. , 21-July-2021
- Mandiant – On the Hunt for FIN7: Pursuing an Enigmatic and Evasive Global Criminal Operation , 1-Aug-2018
- SC Media – Cyber Risk Alliance – FIN7 deploys custom EDR tool on numerous dark web forums , 17-July-2024
- SentinelOne|SentinelLABS – FIN7 Reboot | Cybercrime Gang Enhances Ops with New EDR Bypasses and Automated Attacks , 17-July-2024
- Infoblox – BREAK THE RANSOMWARE SUPPLY CHAIN WITH DNS THREAT INTEL , 31-May-2024
- GitHub – DNStwist: https://github.com/elceef/dnstwist
