Kudos to Meta, EU DisinfoLab, and Graphika for sharing their work on the Russian state-sponsored Doppelgänger influence operations targeting European and U.S. government and media organizations. With an estimate fifty worldwide elections planned in 2024, it difficult to understate the severity of this threat, the goal of which is to destabilize the U.S. and our allies. The anticipated use of adversarial generative AI is likely to intensify effects. In this post, we will provide an overview of Doppelganger operations, demonstrate how tools like DomainTools can be used to counter this threat, summarize recommendations for governance reform in global domain name management, and offer a glimpse of what we might anticipate based on recent trends.
Bottom line up front – campaigns like Doppelgänger exploit systemic weakness in the domain name registration system. Technical countermeasures are available, but insufficient. The financial conflict among the organizations responsible for oversight – ICANN, Domain Registries and Domain Registrars – needs to be acknowledged and addressed. Meta’s recommendations for ‘tackling the domain name abuse problem’ are a call to action for governments, industry, and researchers: [1]

About Doppelgänger: Doppelgänger, a sophisticated foreign influence operation dating back to at least the Russian invasion of Ukraine in 2022, disseminates pro-Russian messaging and disinformation. From 2022 to November 2023, Meta, Graphika, and the EU DisinfoLab have profiled its activities in three major campaigns. [1-3] Attribution is not definitive – Microsoft attributes the Doppelgänger to the actor Storm-1099 [4], Meta attributes it to two sanctioned contractors working for the Russian government (Structura National Technology and Social Design Agency), and others implicate the GRU [10]. The adversary’s objectives and Tactics, Techniques, and Procedures (TTP) in Doppelgänger operations mirror those seen in the Secondary Infektion campaigns, used to influence the US 2016 federal elections. [5]
These campaigns involve registering domain names to impersonate media outlets and government agencies, creating fake news posts, and coordinating inauthentic social media behavior to amplify Russian narratives. The scale of these operations is extensive and ongoing. As of 30-Nov-2023, Meta has blocked over 2,000 Doppelgänger domains and numerous fake accounts and pages.
Understanding Doppelgänger TTP and Threat Hunting: For this analysis, we converted unstructured data from open-source reports by Meta, EU DisinfoLab, and Graphika into structured data using ChatGPT 4.0, enabling us to load it into DomainTools for comprehensive analysis. This process highlighted essential domain features such as domain age, network ownership, and DomainTools risk scores. [6]
Table 1 presents high-risk domains by Registrar, illustrating the adversary’s infrastructure preferences. These insights can inform the development of adversary profiles. The last row, notably, shows many domains with a 100% malicious confidence score from DomainTools, supporting take-down requests to Registrars and hosting providers.
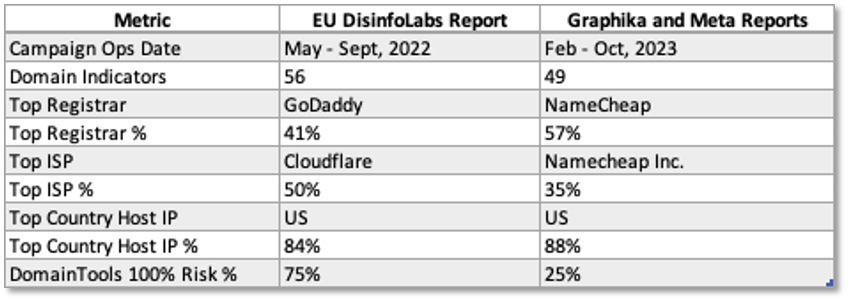
Figures 1-3 display screenshots from DomainTools. Figure 1 shows one of several domains (rrn[.]media) representing the RRN (Reliable Recent News) brand. This site was registered using NameCheap, is hosted in the Netherlands, and has a DomainTools Risk score of 87. [7-8] Figure 2 features electionwatch[.]live, which was registered using the registrar Hostinger, is hosted in the U.S., and has a DomainTools risk score of 72. Figure 3 shows washingtonpost[.]ltd, a spoofed site featuring a fake interview with Ukraine’s President, registered through GoDaddy, hosted in the US by Cloudflare, and a DomainTools Risk score of 100.
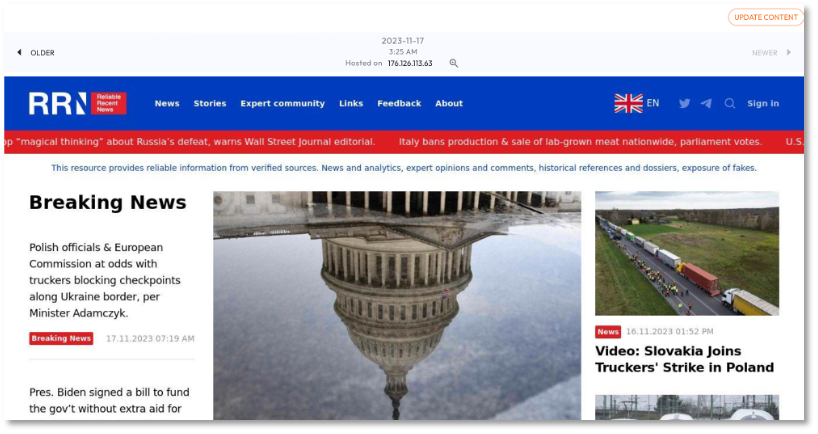
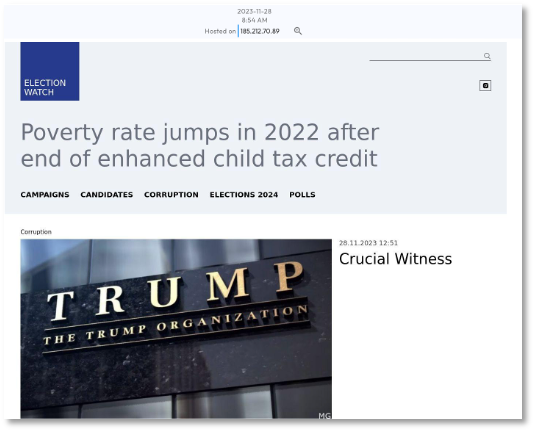
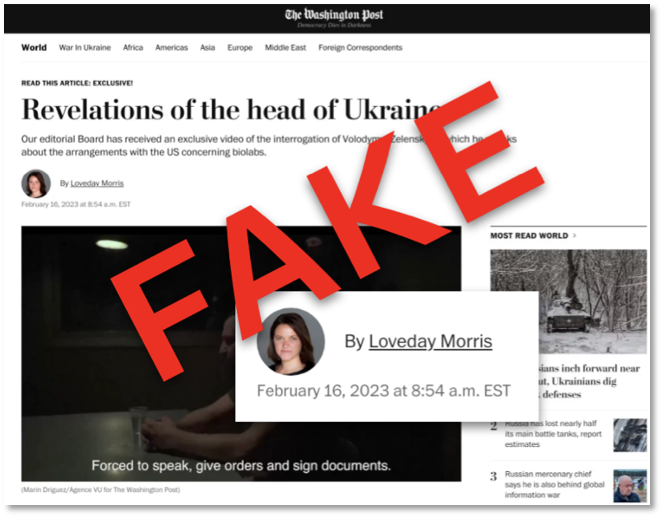
This intelligence from DomainTools helps us understand the adversary’s TTP and build profiles for threat hunting and developing countermeasures.
Policy and Governance: Technical solutions, while necessary, are insufficient in isolation. A comprehensive solution also requires changes in policy and governance of the global system for domain name registration and management. Meta and EU DisinfoLab recommendations, like the ones below, offer a valuable starting point:
- “Domain abuse is one area where existing mechanisms to redress abuse are not sufficient to have material impact at scale. We believe that, in addition to legal and enforcement steps taken by platforms like ours, industry-wide action is needed to protect people against these tactics and raise our collective defenses”
- “Improve ICANN contracts with registrars and registries to take proactive steps to address domain registration abuse at scale, such as to require suspension of customer accounts for known bad actors or impose additional verification for domain names that include a combination of famous brand plus words suggestive of fraud – like “login”, “password”, “security”, “help center”, or “verification”.
- “Adopt laws that require complete, accurate, and verified WHOIS data, similar to Europe’s recently revised Network and Information Systems Directive (NIS2)”.
The U.S., despite its regulatory initiatives in national cybersecurity and trustworthy AI, trails the EU in policies on social media content moderation and disinformation, as noted by the Soufan Center. [11-13]
Evolution and Outlook: If history is any indicator, we can expect more sophisticated foreign influence operations, especially with the advent of AI and generative AI technologies. Recent Russian operations impersonating U.S. celebrities and dissidents underscore this trend. [9, 14, 15]. With elections looming, more proactive and comprehensive defenses are urgently needed.
References
- Meta – Adversarial Threat Report: Third Quarter, 2023 , 30-Nov-2023.
- EU DisinfoLab – Doppelganger Media clones serving Russian propaganda , 27-Sept-2022.
- Graphika – Summit Old, Summit New , Aug-2023
- Microsoft – Russian influence and cyber operations adapt for long haul and exploit war fatigue , 7-Dec-2023
- Graphika – Secondary Infektion, June 2020.
- DomainTools – Iris® Internet Intelligence Platform
- European Council of the European Union – Information manipulation in Russia’s war of aggression against Ukraine: EU lists seven individuals and five entities , 28-July-2023.
- euronews – ‘Doppelganger’: How France exposed a massive Russian disinformation campaign , 15-June-2023
- Wired – Fake Taylor Swift Quotes Are Being Used to Spread Anti-Ukraine Propaganda , 6-Dec-2023.
- Infoblox – Introducing DNS Threat Actors , 9-26-2023.
- Whitehouse.gov – National Cybersecurity Strategy Implementation Plan , July 2023
- Whitehouse.gov – Executive Order on the Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence , 30-Oct-2023
- The Soufan Center – IntelBrief: U.S.-EU Content Moderation Divide Crystallizes with Hamas-Israel Conflict, 7-Dec-2023
- NYTimes – Russia’s Latest Disinformation Tactic Exploits American Celebrities , 7-Dec-2023
- Institute for Strategic Dialog (ISD) “Hey, fellow humans!”: What can a ChatGPT campaign targeting pro-Ukraine Americans tell us about the future of generative AI and disinformation? , 5-Dec-2023

This post shows a great use of DomainTools data.