Blizzards are a normal part of winter news. Notable blizzards and seasons are named. Their targets, frequency, duration, depth, and impact are measured and analyzed. Meteorologists fuse sophisticated weather models from multiple sources to make forecasts. They also examine historical data to provide a context for understanding long-term trends. Local governments use these forecasts to prepare, mitigate, and plan for future seasons.
But hold on. Why does a blog about cyber threat intelligence (CTI) care about blizzards and meteorological methods? We care because cyber blizzards are having their moment. Specifically, Midnight Blizzard and Star Blizzard, two Russian state-sponsored threat groups are currently front page news [1,2] and have been the subject of extensive CTI reporting by Microsoft, RecordedFuture, Google TAG and others for years.
In this post, we share insights on:
- Blizzard Actors and campaigns
- A CTI indicator collection built from recent open-source reports
- Generative AI uses for domain name analysis and research
- DomainTools uses for collection building and threat hunting
- Recent Midnight Blizzard events
Blizzard Actors Intro: CTI researchers use a naming taxonomy for actor groups. The Microsoft taxonomy uses weather themes. The Blizzard family name represents Russian state-sponsored actors. Within the Blizzard family there are 9 actors, including Midnight Blizzard and Star Blizzard. [5]. As researchers choose their own naming conventions, we also need to understand alternative names. For example, Star Blizzard is also known as Seaborgium, Blue Charlie (Recorded Future), COLDRIVER, Callisto and UNC4057 (Google). Midnight Blizzard aliases include NOBELIUM, APT29, Cozy Bear (CrowdStrike), and more.
In this post our focus is on Midnight Blizzard and Star Blizzard for the period 2023 and 2024 as reported by Microsoft [4,7,8], Recorded Future’s Insikt Group [6,9,15] and Google TAG [10]. Midnight Blizzard and Star Blizzard have been active since at least 2008 and 2017, respectively. Both are motivated by espionage and target Western and NATO governments, Ukraine, defense contractors, NGOs, media organizations, and cyber security companies. Notable Midnight Blizzard victims include the U.S. Democratic National Committee (2015), SolarWinds (2019), and Microsoft and HPE (Hewlett Packard Enterprise (2023). Star Blizzard Victims include DOE National Laboratories (Brookhaven, Argonne, Lawrence Livermore). For more on actor profiles see Generative AI Use Case.
Blizzard IOC Collection: The CTI research community is a large and diverse set of producers and consumers. Some CTI researchers share freely on blogs. CTI research from larger organizations is typically licensed through paid subscription services or platforms.
CTI formats and sharing mechanisms vary. Sources may be structured or unstructured. Simple CTI consists of lists with limited context of various indicator types – domain names, IP addresses, file hashes, YARA Rules. High quality CTI provides more indicator context and analysis of campaigns, motivation, TTP (tactics, techniques, procedures), victimology, and mappings to the MITRE ATT&CK framework. As CTI data is not uniform, CTI consumers need to normalize the data to facilitate analysis, reporting, and sharing. Data sharing varies from simple file downloads to automated subscription services.
For this report, we defined:
- actor scope (Star Blizzard and Midnight Blizzard),
- period of analysis (campaigns reported in 2023 and 2024),
- authoritative sources; Recorded Future [6,9,15], Microsoft [4,7,8], Google TAG) [10], and CISA Cybersecurity Advisories [13]
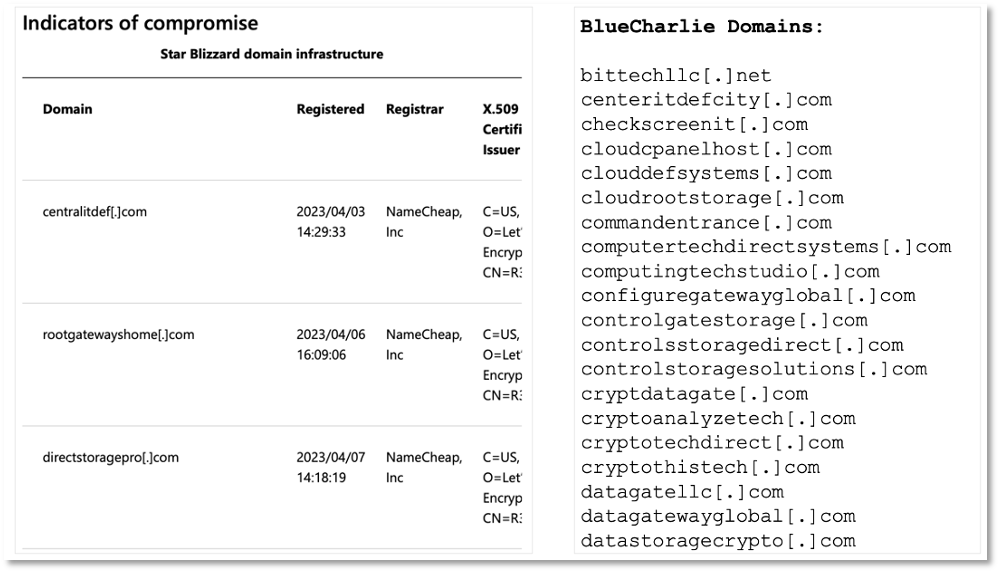
For an example of how unstructured sources of CTI indicators vary consider the simple example shown in Figure 1. On the left is a table extracted from a Microsoft report containing a list of domain names along with 3 ‘enrichment fields’. [8]. On the right is a single column list of domain names from Recorded Future for Actor ‘BlueCharlie’, AKA Star Blizzard. The primary context that makes this data intelligence comes from the source. Enrichment data provides additional context. [9]
For this blog we built a custom CTI collection. A summary of our collection, indicators and sources is shown in Table 1.
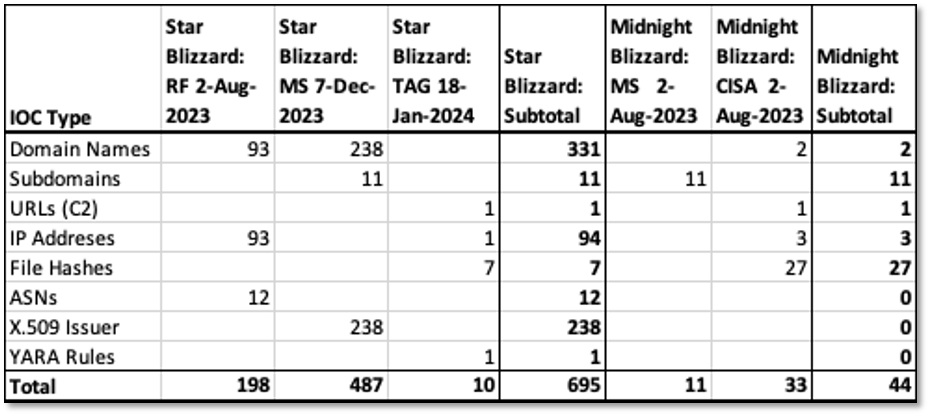
The aggregation of sources and extraction of entities (IOC Types) from the unstructured sources are foundational steps in our analytic process. Subsequent processes – data enrichment, augmentation and normalization – are discussed in the DomainTools Use Case.
Generative AI Use Case: In this section we give two use cases of how a CTI analyst can use Generative AI – ChatGPT 4.0 and Microsoft Copilot (formally Bing Chat Enterprise) – to generate new intelligence.
Use Case 1 – General Research: CTI consumers often aggregate indicators and roll-up intelligence from multiple sources. Even in our simple scenario this involves processing five source reports from three vendors on two campaigns. In Table 1, we discussed the indicator aggregation process. But we also want to fuse and summarize details from adversary profiles described in the source reports. This seemed like a good task for our Generative AI assistant. Unfortunately, we found that it took more prompt iterations to get satisfactory results than we had anticipated.
We began with the same prompt for each assistant, as shown in Figure 2.
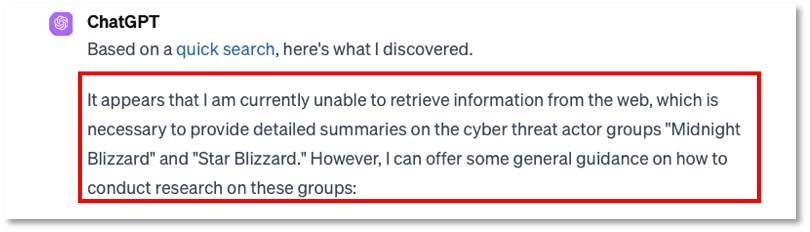
In one case (Figure 3), ChatGPT did not attempt to process the request.
Simplifying our request yielded a better result from ChatGPT as shown in Figure 4.
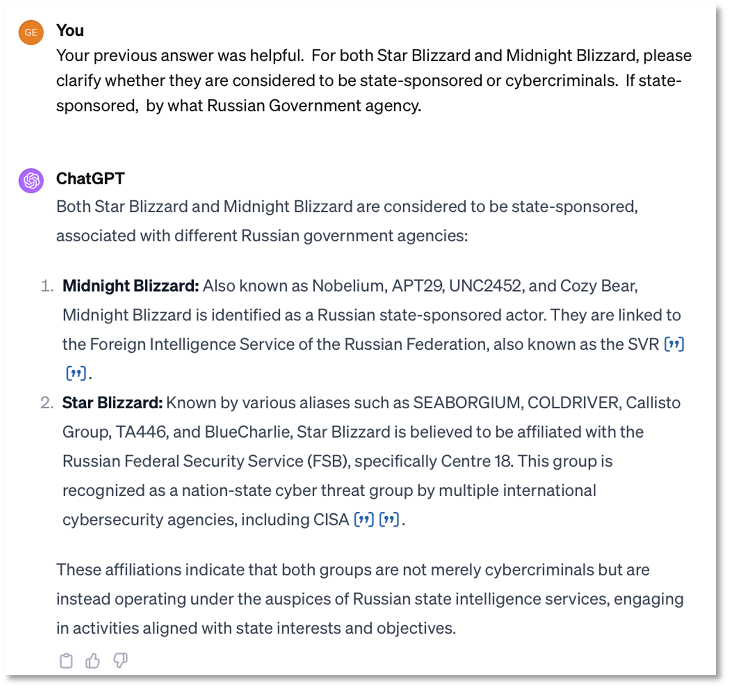
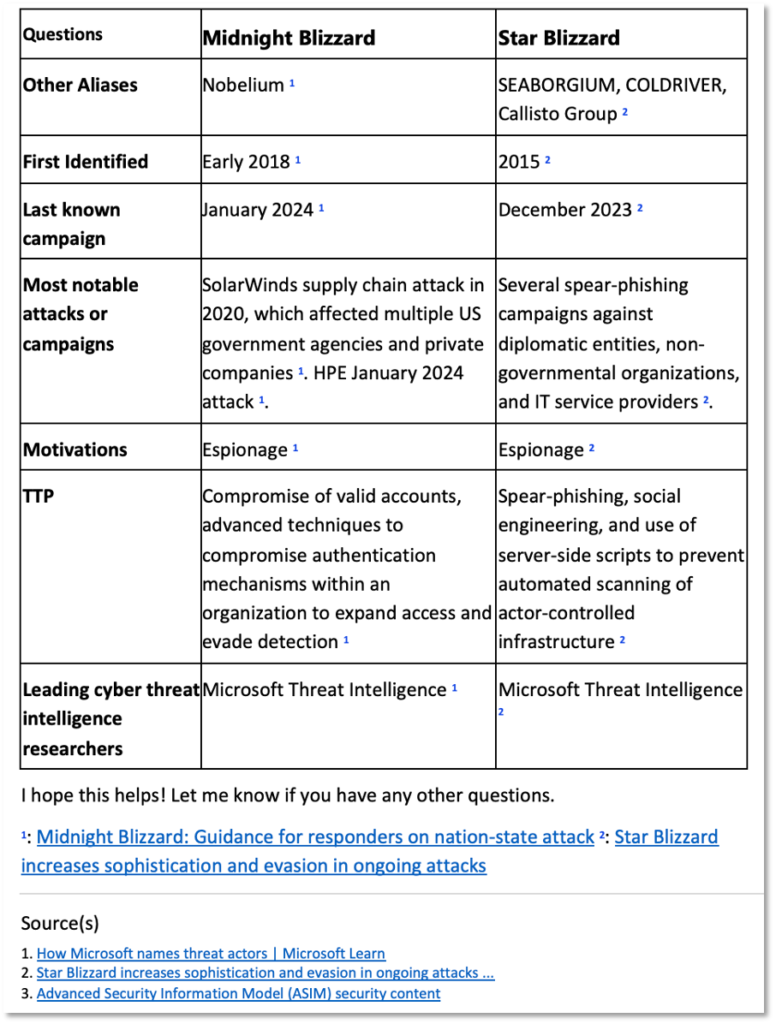
After multiple iterations with Copilot, we got impressive results for a complex request for a table and references. (Figure 5)
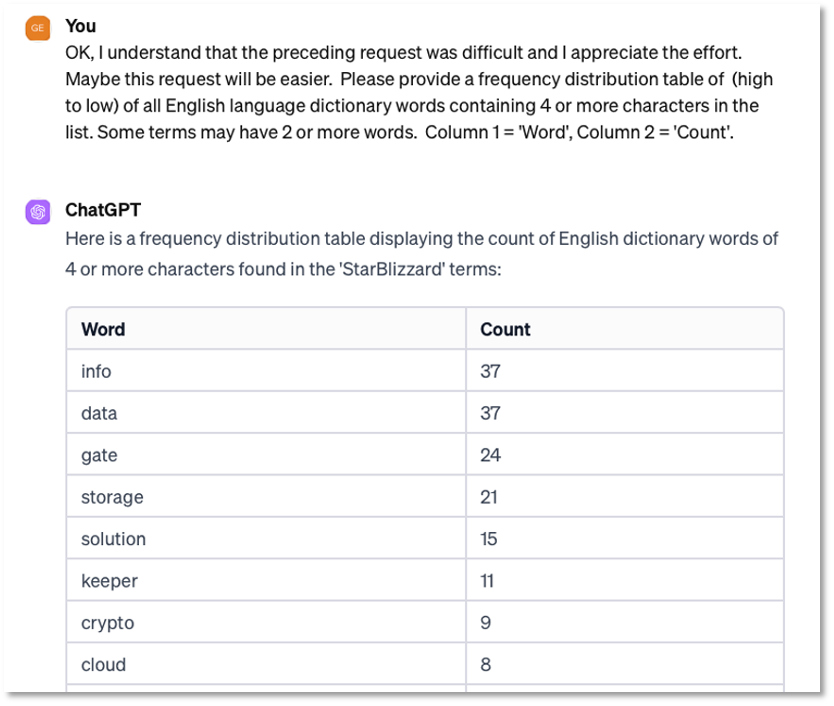
Use Case 2 – Lexical analysis of domain names: Actor patterns can be inferred from domain names and subdomains by analyzing name morphology, use of compounding or hyphens, and themes. For example, Recorded Future’s Star Blizzard report provides term frequency and theme analysis [9], while Microsoft’s report on Midnight Blizzard analyzes “randomized domain generation algorithm (DGA) for actor-registered domains”.
In this use case we tested the ability to assist with basic NLP (Natural Language Processing) analysis of domain names. We were impressed with the ChatGPT results (Figure 6).
DomainTools Use Case: As a discipline, CTI shares principles with the field of information retrieval (IR). Both are concerned with balancing the competing interests of search ‘recall or coverage’ and ‘precision or relevance’. Both seek to optimize coverage while minimizing false positives. In cybersecurity, SOC (Security Operations Center) and Threat Hunt (or threat reconnaissance) Teams may have different precision and recall preferences. To SOC teams overwhelmed with alerts, avoiding false positives (poor precision) is paramount, while Threat Hunt teams may prioritize recall.
The addition of relevant and timely context elevates data to intelligence. Threat Hunt teams use enrichment and augmentation to add context. Domain names are rarely lone wolves, so it is important to find the wolf in order to track the pack. [16] In the following screenshots we show examples of how DomainTools can be used (by human analysts or APIs) to provide relevant context.
Figure 7 shows a single IP address (45.133.216[.]15) from the Google TAG Star Blizzard report. [10] On the left panel, we see pDNS (passive DNS) resolution records of domain names or subdomains to the IP address. On the right the IP Profile shows a risk score for the domains and their resolution history. Below is additional context showing ASN (Autonomous System Number) and geolocation information for the IP. In this case AS4477 Stark Industries is located in Latvia. Note that Recorded Future and Team Cymru associate Stark Industries with malicious activity. [9,17]
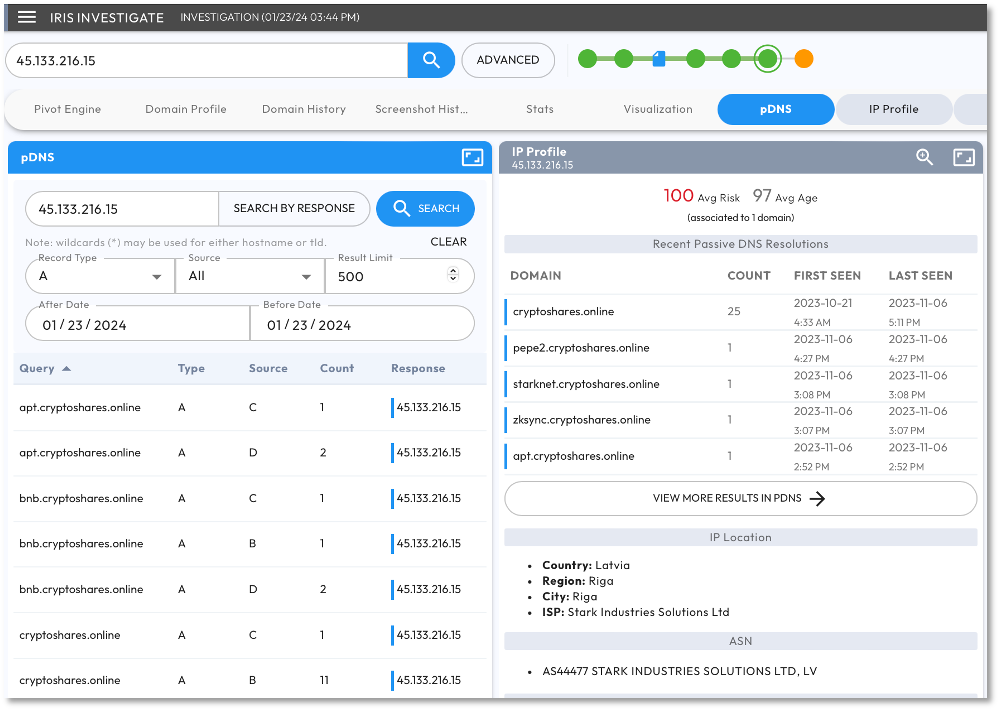
Figure 8 shows domain name indicators (apiwebdata[.]com) extracted from a Microsoft Star Blizzard report. [8] In this example we show context enrichment, augmentation and action. As seen in the bottom left, the associated IP address is an example of enrichment. Using the DomainTools ‘guided pivot’ in the top right we see an example of augmentation with three additional domains resolving to the same IP with a 100% risk score. In the bottom right we show how these domains discovered from augmentation can be tagged for further action.
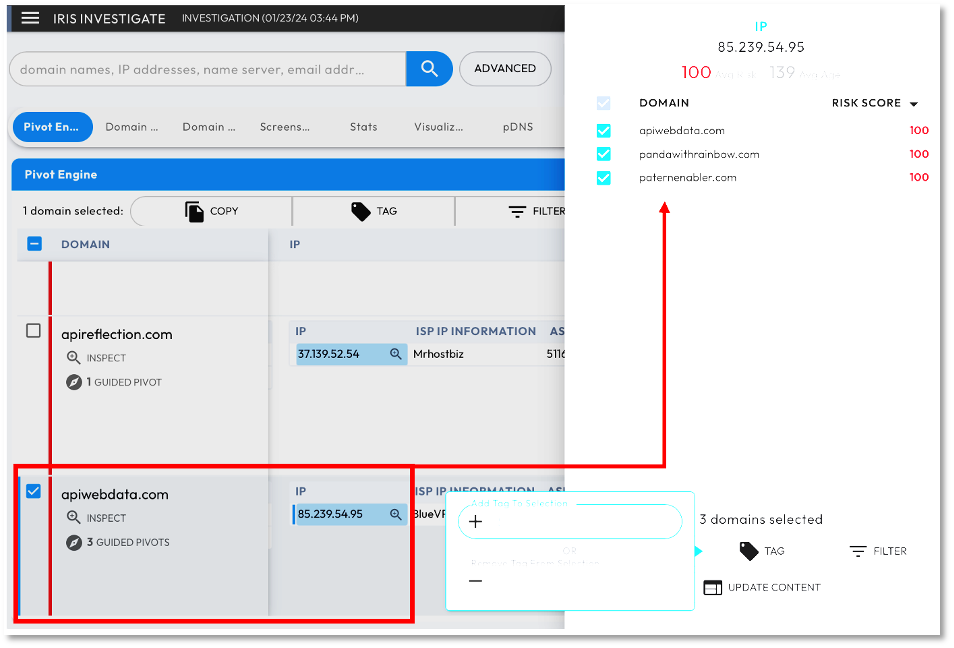
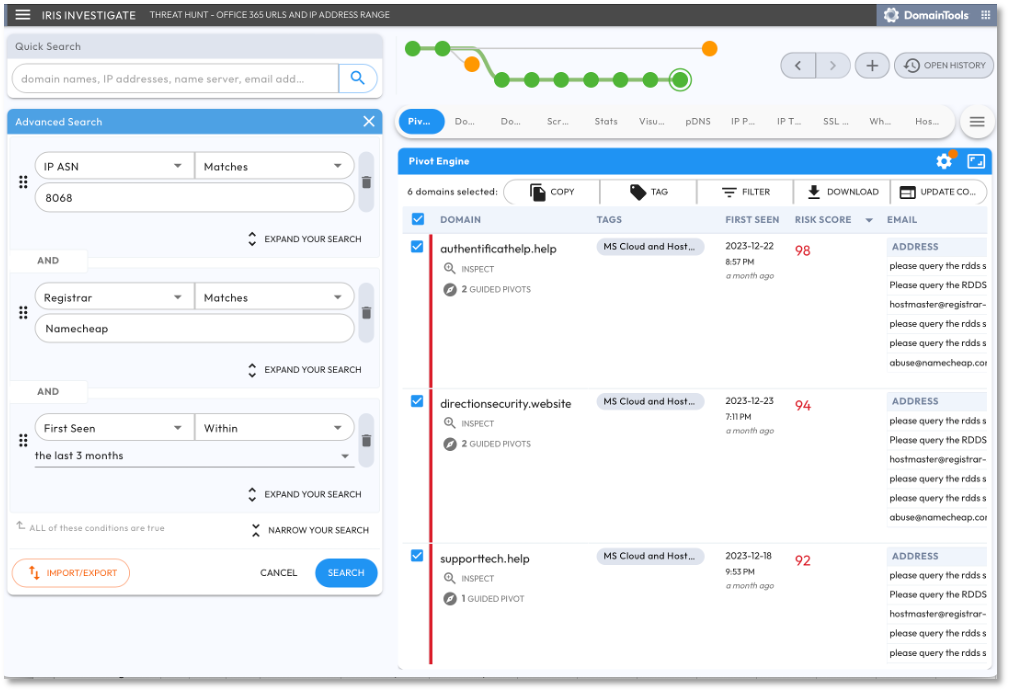
Figure 9 shows a threat hunting scenario using the Advanced Search functions of DomainTools Iris. From our research we learned Star Blizzard and Midnight Blizzard TTP include use of newly registered domain names, the Registrar NameCheap, and ‘tech themed’ domain names or subdomains. And as we learned from the most recently disclosed attacks in the Midnight Blizzard Spotlight, the TTP also targets Microsoft services (SharePoint, Office365, Exchange) on networks registered to Microsoft. In this example, our query specified domains registered: 1) on Microsoft ASN (AS80668), 2) using the Registrar NameCheap, and 3) within the last 90 days. On the right we discovered domains with high risk scores (> 90) and tech themed domain names. As these domains are hosted by Microsoft, are classified as high risk, and match known adversary TTP, these would be good candidates for proactive threat hunting.
Midnight Blizzard Spotlight: Since December 2023 multiple Cybersecurity Alerts have been issued by CISA, US Cyber Command and US allies on Star Blizzard and Midnight Blizzard. [11-13]. On 25-Jan Microsoft guidance for responders notes that Midnight Blizzard “has been targeting other organizations and, as part of our usual notification processes, we have begun notifying these targeted organizations”. [4] Microsoft and HPE (Hewlett Packard Enterprise) have filed attack disclosures to the SEC. [2,14] As we learn more details it seems like we have seen this movie before – initial access leveraging compromised credentials, password spay attacks, targeting of dormant test accounts and OAuth applications, use of security-themed lures, and targeting of Microsoft hosted networks and services. Hopefully vendors and the CTI community have learned lessons from previous attacks that will help contain the spread and impact of this campaign.
References:
- NYTimes – Microsoft Executives’ Emails Hacked by Group Tied to Russian Intelligence , 19-Jan-2024
- Wired – Big-Name Targets Push Midnight Blizzard Hacking Spree Back Into the Limelight, 25-Jan-2024
- Ars Technica – In major gaffe, hacked Microsoft test account was assigned admin privileges, 26-Jan-2024.
- Microsoft – Midnight Blizzard: Guidance for responders on nation-state attack , 25-Jan-2024
- Microsoft – How Microsoft names threat actors , 16-Jan-2024
- RecordedFuture – Russian hackers behind SolarWinds breach accessed emails of senior Microsoft leaders , 22-Jan-2024
- Microsoft – Midnight Blizzard conducts targeted social engineering over Microsoft Teams , 2-Aug-2023
- Microsoft – Star Blizzard increases sophistication and evasion in ongoing attacks , 7-Dec-2023
- RecordedFuture: Insikt Group – BlueCharlie, Previously Tracked as TAG-53, Continues to Deploy New Infrastructure in 2023 , 2-Aug-2023
- Google TAG – Russian threat group COLDRIVER expands its targeting of Western officials to include the use of malware , 18-Jan-2024
- Sixteenth Air Force – Joint Cybersecurity Advisory: US, Allies Highlight Russian-State Cyber Actor “Star Blizzard” Spear-phishing Campaigns, 7-Dec-2023
- National Cyber Security Centre (NCSC) – Advisory: Russian FSB cyber actor Star Blizzard continues worldwide spear-phishing campaigns , 7-Dec-2023
- CISA Cybersecurity Advisory, Alert Code: AA23-347A: – Russian Foreign Intelligence Service (SVR) Exploiting JetBrains TeamCity CVE Globally , 13-Dec-2023
- The Lawfare Institute – The Russian Hack of Microsoft: Lessons for Cybersecurity, 25-Jan-2024
- Recorded Future: The Record – Microsoft says Russian hackers used previously identified tactic to breach senior exec emails , 26-Jan-2024
- DomainTools: Iris Investigate – Track the wolf; Find the pack.
- David Monnier, Team Cymru | Forbes – Threat Intelligence Is Antiquated: Why Business Leaders Should Care , 29-Jan-2024
