This post was initially published 16-Dec-2019 and updated on 27-Dec-2019.
I spend a fair amount of time footprinting and looking at data on country internet topologies, i.e. the size, structure and industry classification of ASNs (Autonomous Systems). One of the things that I look for are routing risks between enterprise ASNs (ASNs that are not ISPs – Internet Service Providers) and ISP ASNs. With persistent tensions between the US and China regarding Internet spying and trade sanctions, I thought it would be an interesting exercise to explore these relationships by analyzing public data on multinational corporation (MNCs) enterprise ASNs that use Chinese ISP ASNs for network peering or transit.
The intent of this exercise is to demonstrate methods of researching and mitigating two types of routing risk – technical risk and inherent risk. Technical risk refers to things like unauthorized route leaks or hijacks, where a leak is a result of an error and a hijack is a result of a malicious unauthorized route announcement. Inherent risk refers to risks presented by upstream routing peers, as upstream peers are able to redirect, block or inspect packets transiting their networks. Inherent risk also considers the implicit value of the data being transmitted.
Preliminary findings from this limited scale exercise were surprising. Recent results from APNIC’s RPKI deployathon suggest that existing tools can help mitigate technical risk. On the other hand, the splinternet trend brought on by wider adoption of national cyber and data sovereignty laws like GDPR (General Data Protection Regulation) in the EU suggests that inherent risk is not a bug but a feature. And further, this risk is not limited to China and it cannot be eliminated. So, with that summary, here’s some background on methods, tools, findings, and suggestions for future research.
Routing relationships can be discovered using tools that monitor BGP listings and activity, from companies like LookingGlass Cyber Solutions (full disclosure – my employer) and Hurricane Electric. The first step in the exercise was to use these tools to enumerate ASNs registered to Chinese entities or located in China. From this we learned that China has the 12th largest country IPv4 Internet in terms of number of ASNs, with 549 active ASNs and 74,749 routing prefixesas of 17-Dec-2019. For comparison, the US is the largest Internet with 19,159 ASNs and 236,557 prefixes.
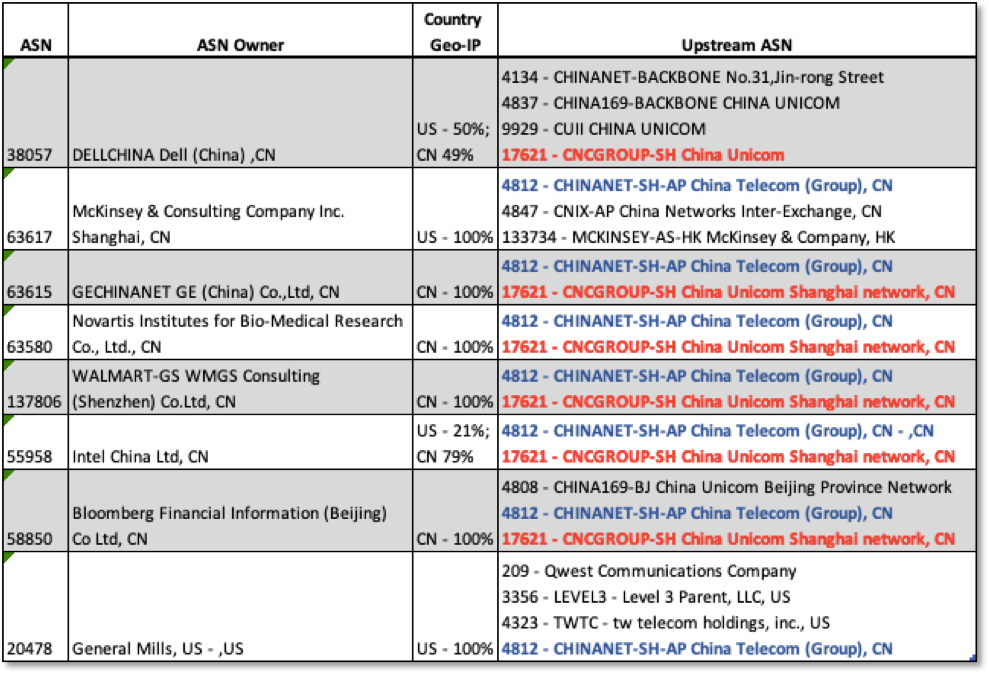
The vast majority of the 549 active ASNs located in China are registered to Chinese companies. We identified 33 ASNs registered to non-Chinese MNCs. These MNCs reveal supply chain and commercial relationships. To simplify, we eliminated enterprises with more than 4 upstream ASN peers. We ended up with a list of 8 enterprises, as shown in the table below. Here are some observations:
- As inherent risk considers the risk profile of the data that the owner may be transmitting or storing, ASN Owner and sector are important factors, particularly in a country known for industrial espionage and intellectual property theft.
- Country Geo-IP is also significant, as country residence and location of host IPs have legal implications. Some organizations are ‘foreign’ subsidiaries operating in China (GE, Novartis, Walmart, Bloomberg); some are foreign subsidiaries in China but with some hosts in China and some in the US (Dell, Intel); and some enterprise hosts are located in the US (General Mills, McKinsey).
- The Upstream ASNs column shows the ASNs used by the MNCs. AS1721 (China UNICOM) or AS4812 (China Telecom) are common to every enterprise ASN in our sample. Further, they appear to function as designated upstream peers for ‘foreign’ enterprise ASNs, as the downstream peering profile of each reveals a relatively high number of foreign MNCs: 33% (14/43) for AS1721 and 51% (28/55) for AS4812.
- General Mills is an interesting case. AS4812 is one of four upstream ASNs and the only Chinese ASN. General Mills network is registered in the US and 100% of the host IPs it announces are geo-coded in the US. Unless a US company is a Chinese subsidiary or a joint venture, or it is announcing IPs located in China, routing upstream through a Chinese ASN is an avoidable risk.
The next step in the exercise was to investigate technical risk. This involved selecting a set of ASNs and setting up BGP monitors that look at changes in peering and prefix announcements, and whether an ASN is using RPKI. For this we used the free version of Cisco BGPmon. For more on technical routing risk, ThousandEyes, Cloudflare and ARIN provide authoritative background on BGP (Border Gateway Protocol) and RPKI (Resource Public Key Infrastructure).
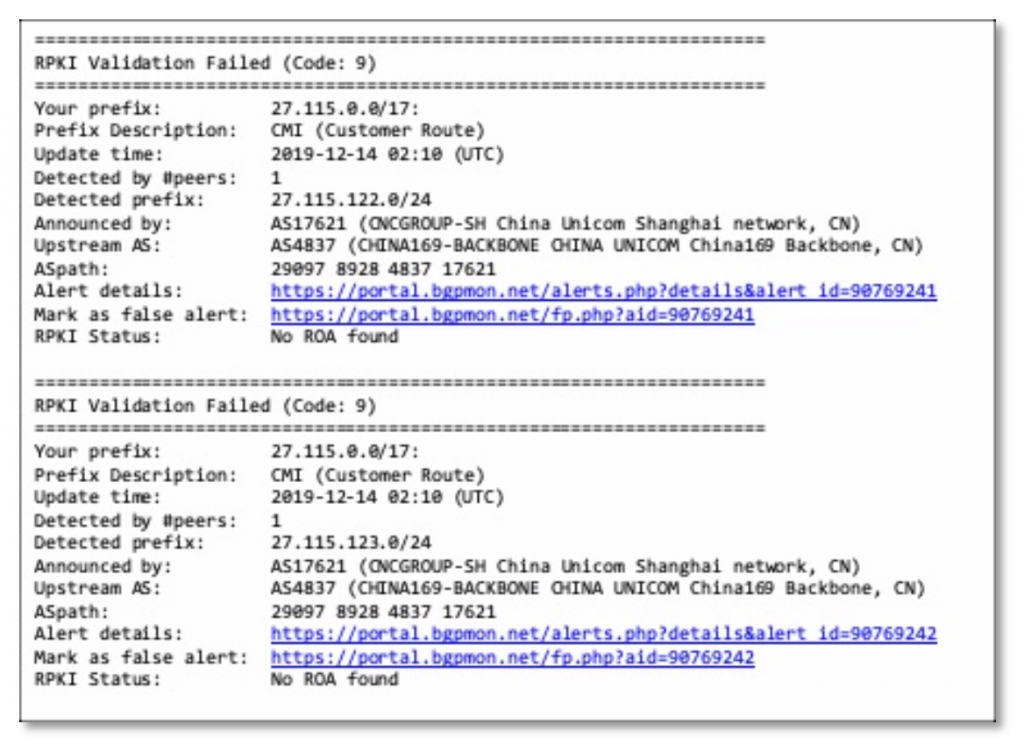
Below is an example of an email alert generated by BGPmon on 13-Dec-2019 for the prefix 27.115.0.0/17. As shown, this prefix is announced by AS17621 China UNICOM. While the alert shows detection of more specific prefixes (27.115.122.0/24), which can be an indicator of route hijacking, this particular alert is for an RPKI Validation failure, with the status ‘no ROA found’. A ROA (Route Object Authorization) is a cryptographically signed X.509 certificate that states that the ASN is authorized to originate a particular prefix or set of prefixes. ROAs are indicators of good routing hygiene and provide an assurance that the prefix is legitimate and has not been leaked or hijacked.
When I started this research I was most interested in technical routing risk as I thought this was the greater challenge. But as my research progressed, I came to see that RPKI, though painfully slow in adoption, has at least the potential to mitigate technical routing risks. In contrast, the more I looked at the rising splinternet trend and cyber sovereignty claims, the more I came to see inherent routing risk as the greater challenge.
To understand the impact of cyber sovereignty and data sovereignty we need to define the terms. The Center for Security Studies (CSS) at ETH Zurich defines cyber sovereignty as the “application of principles of state sovereignty to cyberspace”. Data sovereignty is defined as a “states will to control information generated in or passing through their territory and includes a set of measures employed to achieve that control”.
To manage inherent risk, enterprises should minimize use of peering providers in countries with strong cyber sovereignty laws. Archive360 notes that “Russia, China, Germany, France, Indonesia, and Vietnam require that their citizen’s data must be stored on physical servers within the country’s borders.” Enterprises have to accept that some inherent risk is unavoidable. In such instances, enterprises need to evaluate the sensitivity of the data they store and transmit and employ the strongest encryption possible.
While the risks are greatest in authoritative countries, they are also encountered in advanced and open countries. For example, the Government of Canada’s (GC) white paper on Data Sovereignty and Public Cloud extends the principle of data sovereignty to data in transit and asserts that: 1) all protected data hosted in the cloud be appropriately encrypted while in transit and at rest, and 2) the GC maintain exclusive control of the encryption keys.
From this simple exercise, it is clear that the routing risks are not limited to China. The methods used can be applied to any country. Countries and MNCs should include research of their upstream peering relationships in their risk assessment policies.
