Welcome to the premier episode of cybercrank’s ‘Let’s be frank!, a cybercrank editorial channel that will periodically question generally accepted conventions. Consider it a space where a cybercrank can rant – politely, with reason, and the occasional dash of snark. In this post we’ll review cyber attack models and their limitations.
First, some background on cyber attack models. The philosophy behind these models, as represented by MITRE, is to provide a standardized vocabulary and categorization of common adversary behavior for adversary emulation and intrusion detection research. Here are four well known models:
- the ATT&CK ™ model developed and promoted by MITRE,
- the Cyber Kill Chain® model developed and promoted by Lockheed Martin,
- the Cyber Threat Framework from the US Office of the Director of National Intelligence (ODNI), and
- the Diamond Model of Intrusion Analysis popularized by ThreatConnect and applied by other cyber threat intelligence companies like RecordedFuture.
The inspiration for this post came to me the other day as I was finishing a routine research task that involved mapping methods of a nation-state actor to the MITRE ATT&CK™ model. The actor, ATP28, is politically motivated and employs blended methods including phishing, intrusions, and disinformation against a related group of high-profile targets.
I’ve done many such tasks and have been bothered for some time with two nagging questions:
- How does the ATT&CK model, or any intrusion-centric cyber attack model, accommodate disinformation operations?
- Is mapping to these models worth the time it takes or is just a tedious and superfluous documentation exercise?
Before throwing rocks, I thought I should try to find other voices with similar concerns. I could. Easily. Like this opinion piece from IBM’s Security Intelligence arguing that traditional cyber threat models are in need of modernization. And this research paper from the (CCMWG) Credibility Coalition Misinfosec Working Group, which is actually working on extending the ATT&CK model to support disinformation campaigns with their AMITT Framework. We’ll come back to this in a bit.
Part of my research involved searching Google for matches to the terms, ‘CrowdStrike Burisma’. When I saw the Google results (Figure below) I was surprised that my NewsGuard browser extension, which alerts me to untrusted sources known for unreliable information or even disinformation, flagged (red-highlights) three of the top five results as untrustworthy.
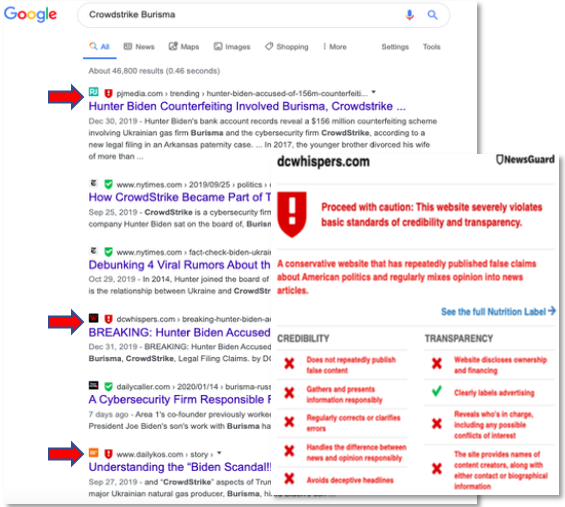
To me, this was just one example of a disinformation indicator that could be relevant to the investigation and should be represented under techniques in the ATT&CK model and mapped to a stage. But as I considered the ATT@CK model, or any of the cyber attack models, it reinforced my belief that these models are just not designed to handle disinformation indicators.
This assessment spurred more research which eventually led me to the AMITT Framework. While AMITT acknowledges limitations of ATT&CK with respect to disinformation, rather than disregarding it, AMITT embraces and extends the ATT@CK model. The figure below of an early version of the AMITT Framework Matrix shows two innovations when compared to the ATT&CK Enterprise Matrix. First, as represented by the stages in the top row of the matrix, AMITT attempts to get left of boom by adding planning and preparation stages which precede the ATT&CK starting stage of Initial Access. In this respect it is similar to the ODNI Cyber Threat Framework, which begins with a preparation stage and provides a planning activity. And second, as shown in the red bounding-box, AMITT introduces a set of new techniques characteristic of information operations which are missing in the ATT&CK Enterprise Matrix.
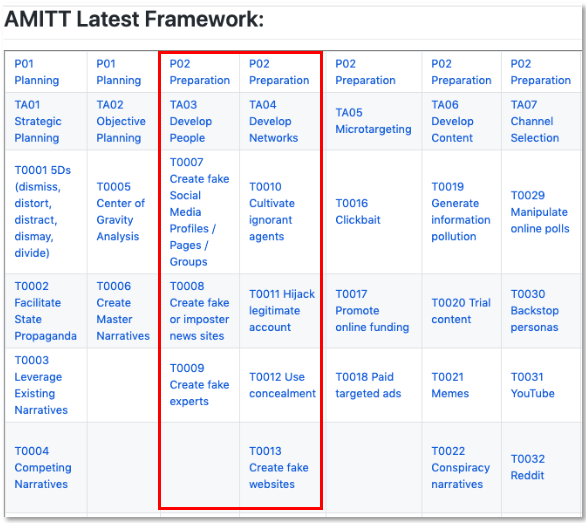
Now back to my two nagging questions; so, what do we think?
Well for the first criticism – limitations for disinformation operations – we’ve just seen that these observations are shared by others. Even better, these limitations are being acted on with efforts like AMITT.
As to the second criticism – that mapping of methods to actors is a tedious, superfluous, and inefficient documentation exercise – I think the criticism is well founded, at least for a threat researcher or analyst trying to complete a quick-hit tactical task. There are two big issues here. First, there’s complexity. The ATT&CK Enterprise Matrix module of the ATT&CK model, defines 11 stages with up to 74 rows totaling 343 possible cell entries! There’s a lot of opportunity to get wrapped around the axle. Second, many of these techniques and tools are common and therefore their association with any particular actor group is weak. Consider – for the group APT28, the model associates 55 techniques and 23 tools. Take one technique – ‘Commonly Used Port’ (T1043). This is associated with 12 different groups or campaigns from multiple nation states. Or take one tool used – ‘Mimikatz’ (S0002). This is associated with 28 Groups and 9 Enterprise Techniques. So just because we can associate a common port or tool with a campaign, if these ports or tools are commonly used by many groups, how confident can we really be in in any assertions we might make using these indicators?
And yet, despite these criticisms, ATT&CK and other cyber attack models are still useful and necessary. The richness and complexity of ATT&CK may have drawbacks for tactical research tasks, but such detail is beneficial for academic researchers and software architects. And while the Enterprise module of ATT@CK may be limited and cumbersome for some, the Groups module is a comprehensive and authoritative reference model that make it an essential piece in the cyber intelligence researcher’s toolkit.
