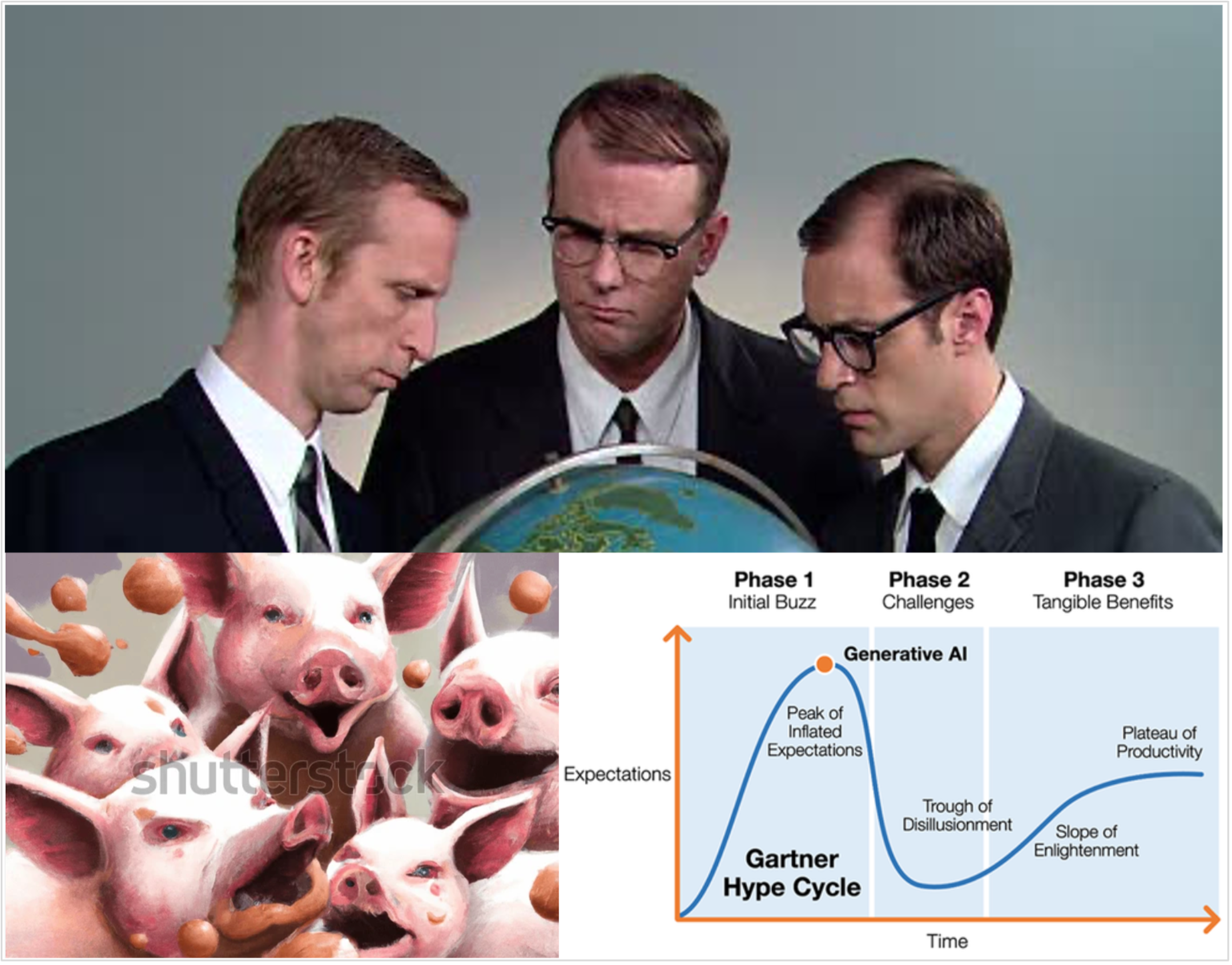
Initially, this post was intended to be a routine review of how cyber threat actors utilize domain names and DNS infrastructure, how these uses evolve, and how cyber threat analysts can use …
Bulletproof Hosting Havens for FIN7 and Russian Cyber Threat Groups arrow_forward