This article began as a review of phishing and oversight failures in .US domains. It awakened my memory of Paul Vixie’s prescient 2010 admonition to ‘take back DNS’ and assertion of the simple truth that most new domain names are dreck or malicious. [1] Eleven years later, the problems enabled by malicious domains – phishing, ransomware, cybercrime, disinformation – have become a crises that demands a comprehensive response combining technical countermeasures, governance reform, and a more rigorous regulatory framework.
Technology alone is not the answer. While technical solutions like domain reputation scoring and DNS firewalls do help [2-3], generative AI threatens to exacerbate the problem. To fix the problem, we need to confront the core issue – weak and conflicted governance standards, practices and enforcement. All entitles involved in governance – GoDaddy Registry operations, the Domain Registrars, and ICANN – depend on domain sales for their funding. Security is subordinated to domain sales. [4-8] It doesn’t have to be this way. Comparative analysis of phishing levels in more regulated ccTLDs (country code Top Level Domains) in Europe vs .US provides clear evidence that strong governance works. [11]
Since August 2023, the .US domain landscape has come under scrutiny for its alarming levels of phishing from respected authorities on DNS. [9-12] Criticisms have noted lax enforcement of the US Nexus registration policy by the National Telecommunications and Information Administration (NTIA), with GoDaddy Registry Operating Company LLC acting as the NTIA’s administrative arm. A highly critical report from KrebsonSecurity casting .US domains as a ‘phishing cesspool’, coupled with NTIA’s claims of prioritizing DNS abuse and evidence-based policy, sparked my quest for more evidence. Using DomainTools’ Iris Investigate [13], I found more evidence easily.
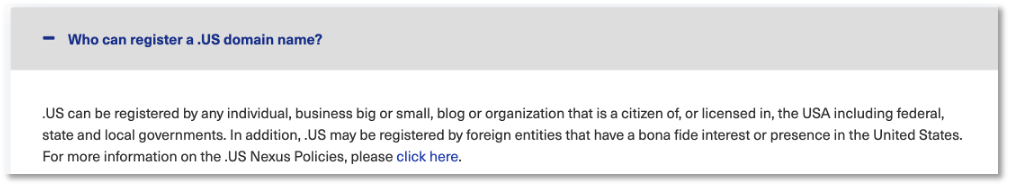
Before we dig into the findings, we need some context on actual US Nexus policy. As shown in Figure 1, the policy guidance is brief and general. In the more detailed policy in [2], it is clear that registrant policy enforcement is delegated from the Registry (GoDaddy) to the Registrants and Registrars. As noted by KrebsonSecurity, ‘whatever GoDaddy is doing to manage that vetting process isn’t working’. [11]
The first step was to select all domains in the .US TLD created between 9-1-2023 and 11-6-2023. This came to 79,000. We then filtered on domains with a risk score of 90 or higher, based on a scale of 0 – 100. We found 9,500 (12% of total domains) high risk domains, where risk is a computed score by DomainTools based on malicious behaviors (phishing, malware, spam). Selected findings from this collection of domains follow.
Malicious Domains hosted in Russia or non-US countries: We found 61 domains were hosted in Russia. It is hard to imagine what the ‘bona fide interest or presence in the United States’ for these domains might be. For these Russian hosted domains, 2 of the registrants were located in Russia and 20 were located outside the U.S.
Bogus Email Addresses: When we looked at the email addresses at least 13 raised flags with names like ‘ddosguard2022p’ (Russian DDoS service provider), trustme2288, and deathb4dishonor5358.
NameSilo Registrar Domains: Infoblox noted that NameSilo is the registrar of choice for the threat actor Prolific Puma, a prolific abuser of the .US ccTLD [12]. Ten of the NameSilo domains hosted in Russia use the same Russian ISP, DDoS-Guard LLC.
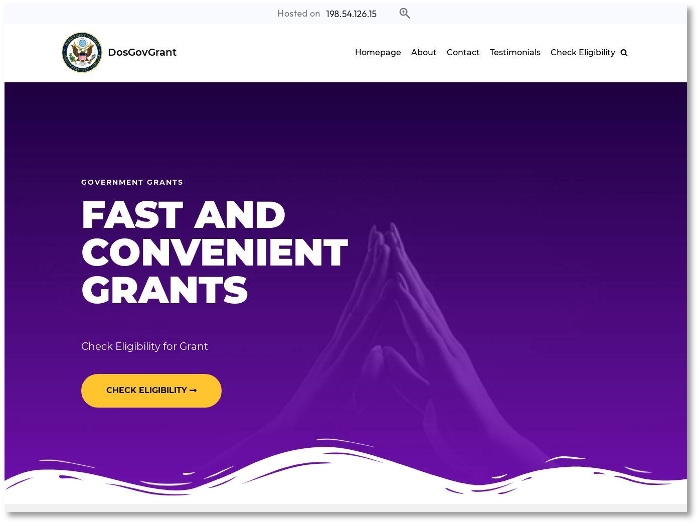
Domain names targeting Gov sites or users: It is ironic that the only ccTLD under the authority of a US federal government agency (NTIA is an agency under the US Department of Commerce) is used by cybercriminals to attack government sites and/or brands. We found 33 high-risk domains targeting users of government services (grants, contracts, bids) and federal agencies (IRS, Federal Reserve, Treasury, Social Security). Figure 2 shows a scam website posing as a non-existent federal agency (DosGovGrant). The phishing domain, dosgovgrant[.]us, was created on 10-10-2023, has a DomainTools phishing score of 95, and was registered through the Registrar NameCheap.
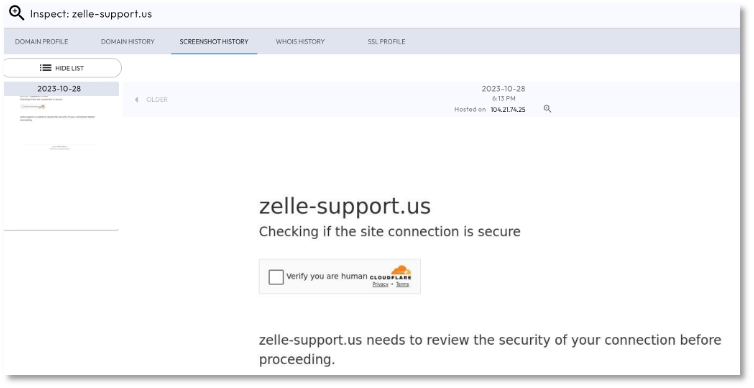
Phishing themes: Filtering on strings in domain names, we identified targeted themes and brands. For example, 390 domains targeted ‘cloud’ providers, 211 domains targeted ‘support’ functions and 14 targeted Apple. Figure 3 shows an example of a phishing website, zelle-support[.]us, impersonating the payment App company Zelle, a frequent target of scammers. [14] The phishing domain was created on 10-28-2023, has a DomainTools phishing score of 100, and was registered through the Registrar NameSilo. The registrant used the disposable email address service, yopmail[.]com, a favorite of scammers.
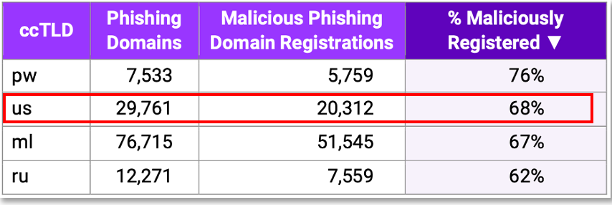
We’ll conclude with a look at how .US compares with other ccTLDs. Table 1 from the Interisle Report [9] shows that .US ranks second among ccTLDs with at least 5,000 registrations over the past year in both the total number of phishing domains (29,761) and the % of maliciously registered domains (20,312). This puts the .US ccTLD in a peer group with Palau (PW) and Mali (ML) – two ccTLDs considered to be phishing havens – and Russia (RU). Another indication of poor comparative performance is provided by KrebsonSecurity, noting that “virtually all European Union member state ccTLDs that enforce nexus restrictions also have massively lower levels of abuse due to their policies and oversight”, creating a situation that ‘should not be acceptable to the U.S. government overall, nor to the US public.’ [11]
References
- Paul Vixie – Taking Back the DNS , 14-July-2010.
- Infoblox – Farsight Security and Infoblox Provide Zero-Hour Protection Against Cyberattacks Due to New Domains , 14-June-2017.
- Palo Alto Networks – Palo Alto Networks Introduces Fastest-Ever Next-Generation Firewall and Integrated Cloud-Based DNS Security Service to Stop Attacks, 12-Feb-2019.
- Registry Services LLC (GoDaddy Registry) – usTLD Nexus Requirements Policy , 2021.
- GoDaddy – .US Registry – FAQ
- Registry Services LLC: usTLD Nexus Requirements Policy , 2021.
- ICANN – Resources for Country Code Managers
- NTIA – Comments on usTLD WHOIS Federal Register Notice (5.1.23) , 7-25-2023.
- Interisle Consulting Group – Phishing Landscape 2023 , 8-9-2023.
- Cybercrime Information Center (Interisle Consulting)
- Krebsonsecurity.com – Why is .US Being Used to Phish So Many of Us? , 9-1-2023.
- Infoblox – Prolific Puma: Shadowy Link Shortening Service Enables Cybercrime , 10-31-2023.
- DomainTools – Iris Investigate
- FTC (Federal Trade Commission) – Do you use payment apps like Venmo, CashApp, or Zelle? Read this , 10-14-2023.
- Infoblox – Introducing DNS Threat Actors , 9-26-2023.
