The question isn’t novel or fanciful. It was the subject of a McAfee blog post in the run-up to the US 2018 midterm elections. And in the DOTGOV Online Trust In Government Act of 2019, Congress has proposed that DHS CISA (Cybersecurity and Infrastructure Security Agency) assume responsibility for the ‘.gov’ domain registry operations from the General Services Administration (GSA). The goal is to provide the policies, infrastructure, funding and incentives needed to accelerate ‘.gov’ adoption by state and local entities as a security measure. In this post, we’ll consider the rationale, merits, benefits and challenges of these proposed changes in Internet governance policy. And we’ll review some real-world data and examples.
To be clear, all eligible US governmental entities – federal, state, local, tribal – should switch and redirect their domain names to ‘.gov’. At a minimum, ‘.gov’ domains provide greater protection from disinformation and impersonation. Unlike other gTLDs (general top-level-domains), which do not require validation or disclosure of the registrant organization, ‘.gov’ domain registration is validated and publicly disclosed. With the US 2020 elections upon us, there is an urgent need to harden state and local government websites, particularly those providing election-related information and services.
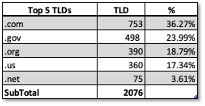
Presently less than 13% ( 5,000 of 39,000) of US local governments are using ‘.gov’ domains, according to StateScoop. A TLD distribution specifically for election-related websites is shown in Table 1. The data is based on a sample of 2,076 election related FQDNs (Fully Qualified Domain Names) from LookingGlass Cyber Solutions (full disclosure – LookingGlass is my employer). With approximately 8,800 voting jurisdictions in the US, this represents a large sample with close to 24% coverage. The vast majority of these FQDNs are for local (county and town) entities. Of the 498 ‘.gov’ FQDNs we reviewed, about seventy (14%) are second-level domains (SLDs) with the remainder representing subdomains. As shown, only 24% of election-related websites are using ‘.gov’ domains.
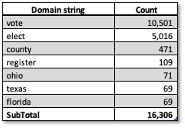
To get a sense of the potential threat of ‘non-gov’ domain names to the 2020 elections, we reviewed election related Newly Registered Domain (NRDs) names for the past 12-months (6-24-2019 to 6-23-2020), in a similar manner as described in our Covid19 NRDs in our posts of 17-April-2020 and 23-April–2017. During this period, we detected more than 26,000 newly registered election-related domains, of which 8,300 are live (resolving to an operational website). Table 2 provides an indication of the targeting of these NRDs based on simple string matching in the domain names. (note – some domains contain multiple strings). None of these TLDs are ‘.gov’. While some of these domains are legitimate, a cursory review shows many domains of unknown provenance, presently parked, or suspicious. Parked or dormant domains are still a concern and need to be monitored, as they could be activated shortly before the elections to spread disinformation or to suppress the vote.
The following scenario shows challenges that users face in assessing trust in the absence of clear signals such as ‘.gov’ domains. From our NRD list, we selected two lexically similar ‘.com’ domain names, both appearing to be associated with Allegheny County, in the swing state of Pennsylvania.
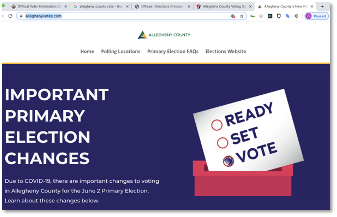
The domain alleghenyvotes[.]com was registered on 16-Jan-2020. As shown in Figure 1, the website looks legitimate based on content, appearance and structure. But as it is easy to spoof websites, the user has to dig deeper to confirm legitimacy. In this case a whois look-up shows the Registrant Organization as County of Allegheny. On this basis, we assume the site is legitimate.
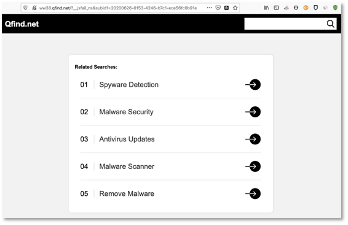
Now consider a similar domain name, alleghenycountyvotes[.]com. This was registered on 1-June-2020. As of 25-June, attempts to resolve the domain result in a redirect to the site shown in Figure 2. As the domain we landed on is not the domain we queried, and the redirected landing site is attempting to get the user to click a link, it is clearly suspicious. Whois analysis shows a private registration, making it difficult to assess who is behind it. Further analysis shows the domain host IP as 103[.]224[.]182[.]242 and hosted in Australia by ASN 133618 – TRELLIAN-AS-AP Trellian Pty. Limited, AU. The host IP is currently reported on threat feeds as a Spyware Server.
Domain names are soft targets in our critical infrastructure; easily impersonated and exploited for disinformation. As such the proposed changes in the ‘.gov’ registry governance, policy and funding, are a pragmatic and necessary step towards blunting the threat to our elections from disinformation and impersonation. But as KrebsonSecurity points out, CISA needs to fix lax verification policies and processes as presently practiced by GSA. If these countermeasures are to have any effect in the US 2020 election, CISA must move quickly on the design and implementation of tight registration policies with strong system and support infrastructure.
